Toymaker’s website pushes ransomware that holds visitors’ files hostage
Enlarge (credit: Malwarebytes)
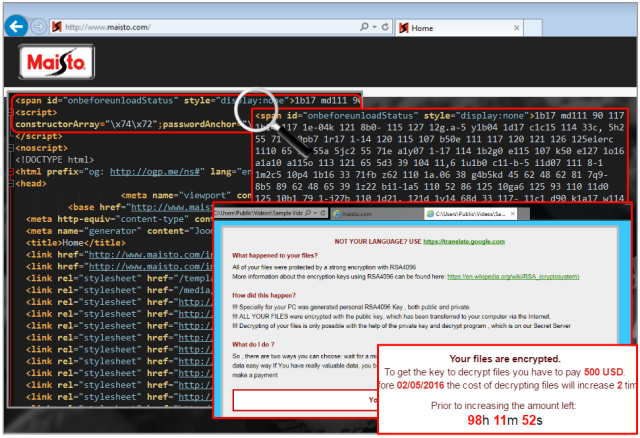
The website belonging to Maisto International, a popular maker of remote-controlled toy vehicles, has been caught pushing ransomware that holds visitors’ files hostage until they pay a hefty fee.
Malicious files provided by the Angler exploit kit were hosted directly on the homepage of Maisto[.]com, according to antivirus provider Malwarebytes. The attack code exploits vulnerabilities in older versions of applications such as Adobe Flash, Oracle Java, Silverlight, and Internet Explorer. People who visit Maisto[.]com with machines that haven’t received the latest updates are surreptitiously infected with the CryptXXX ransomware. Fortunately for victims in this case, researchers from Kaspersky Lab recently uncovered a weakness in the app that allows users to recover their files without paying the extortion demand. People infected with ransomware in other drive-by attacks haven’t been so lucky.
After discovering the infection of the Maisto homepage, Malwarebytes Senior Security Researcher Jerome Segura used this tool from website security firm Sucuri. It detected that Maisto was running an out-of-date version of the Joomla content management system, which is presumed to be the way attackers were able to load the malicious payloads on the homepage.