Viasat Hack Tied to Data-Wiping Malware Designed to Shut Down Modems
Last month’s massive Viasat satellite internet outage has been connected to malware capable of wiping data from modems and routers.
Cybersecurity firm SentinelOne says it spotted a malware sample that was likely used during the Feb. 24 Viasat hack, which disrupted internet service. The malware, dubbed AcidRain, is a Unix executable program designed to target devices built with the MIPS architecture.
SentinelOne noticed the malware after a sample of AcidRain was uploaded to malware-detection service VirusTotal on March 15. The same sample came from Italy, where SkyLogic, the Viasat operator managing the affected network, is also based. In addition, the malware sample was labeled with the name “ukrop,” a possible reference to Ukraine Operation.
(SentinelOne)
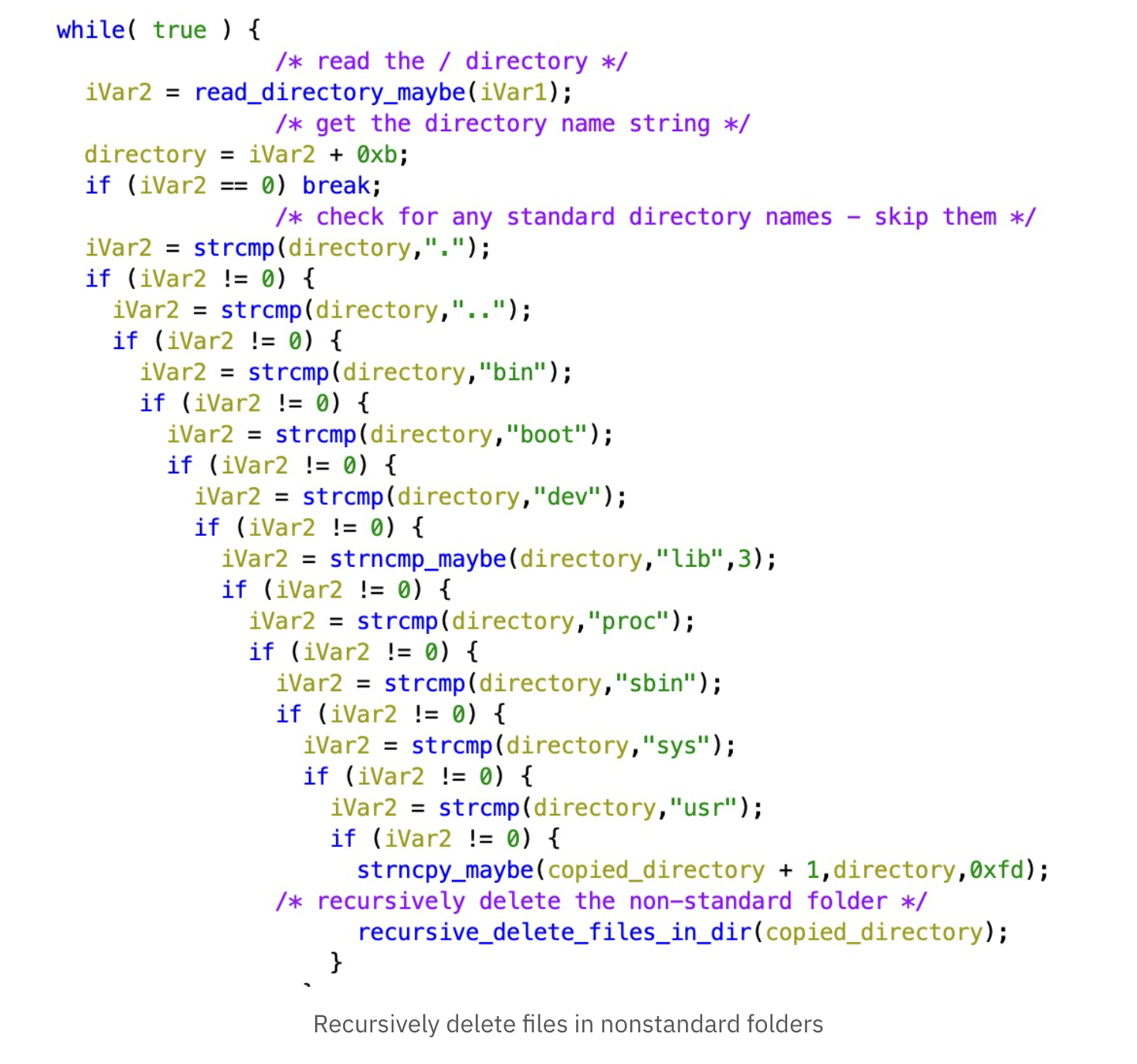
SentinelOne also examined AcidRain and found it can perform “an in-depth wipe of the filesystem and various known storage device files” on an infected modem. The malware will then trigger a reboot, leaving the device inoperable.
The security firm issued the report a day after Viasat provided more details about the Feb. 24 outage, which occurred right as Russia began to invade Ukraine. The disruption caused thousands of users in Ukraine and tens of thousands more across Europe to temporarily lose internet access.
Viasat’s investigation found the hackers behind the incident exploited a misconfigured VPN device to gain remote access to the satellite internet infrastructure, and then used “legitimate, targeted management commands” across a large number of modems to knock them offline.
However, Viasat’s investigation made no mention of any data-wiping malware. Instead, the company’s report pointed to “destructive commands” overwriting key data in flash memory on the affected modems, rendering them useless.
Still, Viasat isn’t denying SentinelOne’s findings about AcidRain. In a statement, the satellite internet provider said: “The analysis in the SentinelLabs report regarding the ukrop binary is consistent with the facts in our report—specifically, SentinelLabs identifies the destructive executable that was run on the modems using a legitimate management command as Viasat previously…