Vodafone’s ho. Mobile admits data breach, 2.5m users impacted

Vodafone Group’s low-cost operator ho. Mobile announced that hackers stole part of its customer database thus obtaining personal user information and SIM technical data.
The stolen database, offered for sale on dark web forums since December 22, has been partially verified and includes sufficient details to carry out SIM-swap attacks, putting at risk about 2.5 million subscribers.
Free SIM card replacement
News of the database being peddled on a hacker forum emerged on December 28 from researcher Bank Security. An initial statement from the mobile operator informed that it had no evidence of illegal access to its systems.
This changed on Monday when the company confirmed the massive breach saying that personal data and SIM-related information had been stolen.
The operator says that the hackers got customers’ name, surname, phone number, email, date and place of birth, nationality, and address. They also have the SIM Integrated Circuit Card Identification Number (ICCID) – a unique number providing the card’s country, home network, and identification.
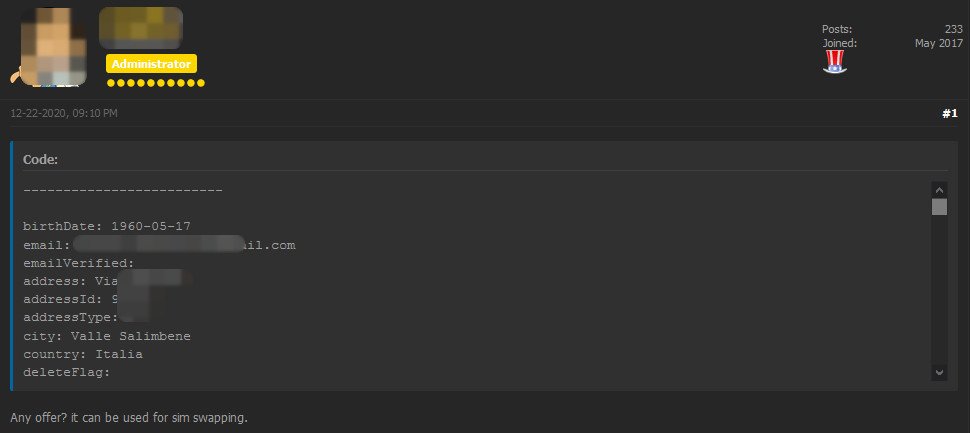
Combined, these details can be used for SIM-swapping attacks that enable hackers to assign a victim’s phone number to a SIM card in their possession and thus receive the target’s calls and text messages.
Bank Security provides a list of the details present in the database stolen by hackers:
Here an example of the stolen data:
– fiscal Code
– phone Number
– sim Iccid
– address
– cityHere the full list:https://t.co/RrlTMITLpc pic.twitter.com/4byhYnNT4n
— Bank Security (@Bank_Security) December 28, 2020
At least one actor may have purchased the database, while several others showed interest.
In a comment on the hacker forum, one user says that the seller asked for $50,000 for the entire database. Even if not sold in bulk, the seller could break it into smaller sets to obtain a profit.
Using the sample data from the seller, several researchers were able to confirm that the database was real by contacting victims.
The mobile operator is now trying to minimize the impact of the breach on customers and is offering them a new SIM card free of charge.
With the risk of a swap still looming, the SIM replacement process requires…


