Who DDoS-ed Georgia/Bobbear.co.uk and a Multitude of Russian Homosexual Sites in 2009? – An OSINT Analysis
NOTE:
I took these screenshots circa 2009.
UPDATE:
Here are some of the related botnet C&C server domains known to have been involved in the campaign:
hxxp://cxim.inattack.ru/www3/www/
hxxp://i.clusteron.ru/bstatus.php
hxxp://203.117.111.52/www7/www/getcfg.php (cxim.inattack.ru)
hxxp://cxim.inattack.ru/www2/www/stat.php
hxxp://cxim.inattack.ru/www3/www/stat.php
hxxp://cxim.inattack.ru/www4/www/stat.php
hxxp://cxim.inattack.ru/www5/www/stat.php
hxxp://cxim.inattack.ru/www6/www/stat.php
hxxp://finito.fi.funpic.org/black/stat.php
hxxp://logartos.org/forum/stat.php – 195.24.78.242
hxxp://weberror.cn/be1/stat.php
hxxp://prosto.pizdos.net/_lol/stat.php
hxxp://h278666y.net/www/stat.php – 72.233.60.254
I’ve decided to share this post including related screenshots and technical details with the idea to inspire everyone to continue doing their research including cyber attack and campaign tracking and monitoring including cyber attack and cyber attack campaign attribution efforts.
Back in 2009 there was a major speculation that Russia indeed launched a massive DDoS (Distributed Denial of Service) attack against Georgia which was in fact true. What was particularly interesting about this campaign was the fact that the same DDoS for hire including the managed DDoS service that was behind the attack was also observed to launch related DDoS attack campaigns against bobbear.co.uk including a multi-tude of Russian homosexual Web sites where the actual Web sites indeed posted a message back then on their official Web sites signaling the existence of the DDoS attack targeting their Web sites.
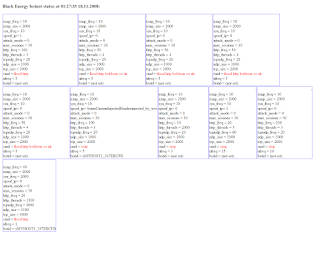
Who was behind the campaigns? An image is worth a thousand words including the actual use of the original Maltego Community Edition back then which used to produce outstanding results in a variety of cases and cyber attack incidents and campaigns.
Sample screenshots include:
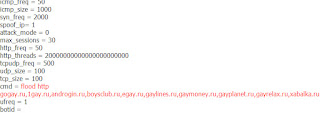
Sample DDoS C&C domains known to have been involved in the campaign include:
hxxp://emultrix.org
hxxp://yandexshit.com
hxxp://ad.yandexshit.com
hxxp://a-nahui-vse-zaebalo-v-pizdu.com
hxxp://killgay.com
hxxp://ns1.guagaga.net
hxxp://ns2.guagaga.net
hxxp://ohueli.net
hxxp://pizdos.net
Sample DDoS C&C domain URLs…