10 Botnet Detection and Removal Best Practices
If your device suddenly behaves like a re-animated zombie, you might be under a Botnet attack.
Also known as a zombie army, these attacks involve hijacking internet-connected devices infected with malware, controlled remotely by a single hacker. The scale of these attacks is immense, as demonstrated by a cyber assault that exploited 1.5 million connected cameras to overwhelm and take down a journalist’s website.
As the IoT market grows exponentially, reaching 75.4 billion devices by 2025, the need for robust botnet detection and removal becomes critical for digital safety.
How Does a Botnet Attack Work?
A botnet functions as a network of compromised devices, each under the control of a malicious actor. Typically, these devices become infected unknowingly through activities like visiting a malicious website, where malware is automatically downloaded without the user’s awareness. Once compromised, a device becomes part of the botnet, essentially a collective of hijacked devices.
The lifecycle of a botnet involves several key stages:
Infection
The process begins with the initial infection of individual devices. This can occur through various means, such as users unknowingly downloading malware from malicious websites, falling victim to phishing schemes, or exploiting vulnerabilities in software.
One prevalent method involves the mass sending of phishing emails to target systems. These phishing schemes can be challenging to detect, even for vigilant users and advanced alert systems. The insidious nature of malware lies in its ability to infiltrate devices, unpack viruses, and take control, often without the user’s knowledge.
Propagation
Once a device is infected, it becomes part of the botnet and can be used to propagate the malware further. This can involve exploiting known software vulnerabilities, enabling the botnet to rapidly expand its reach by infecting other vulnerable devices.
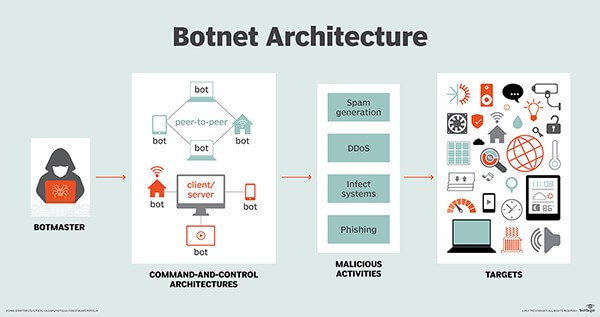
Command and Control (C2)
The botmaster establishes control over the compromised devices through a command-and-control server (C2). This server serves as the central hub for communication between the botmaster and the infected devices. The botmaster can issue commands to the entire botnet or…