Breaches by Iran-affiliated hackers spanned multiple U.S. states, federal agencies say
HARRISBURG, Pa. — A small western Pennsylvania water authority was just one of multiple organizations breached in the United States by Iran-affiliated hackers who targeted a specific industrial control device because it is Israeli-made, U.S. and Israeli authorities say.
“The victims span multiple U.S. states,” the FBI, the Environmental Protection Agency, the Cybersecurity and Infrastructure Security Agency, known as CISA, as well as Israel’s National Cyber Directorate said in an advisory emailed to The Associated Press late Friday.
They did not say how many organizations were hacked or otherwise describe them.
Matthew Mottes, the chairman of the Municipal Water Authority of Aliquippa, which discovered it had been hacked on Nov. 25, said Thursday that federal officials had told him the same group also breached four other utilities and an aquarium.
Cybersecurity experts say that while there is no evidence of Iranian involvement in the Oct. 7 attack into Israel by Hamas that triggered the war in Gaza they expected state-backed Iranian hackers and pro-Palestinian hacktivists to step up cyberattacks on Israeli and its allies in its aftermath. And indeed that has happened.
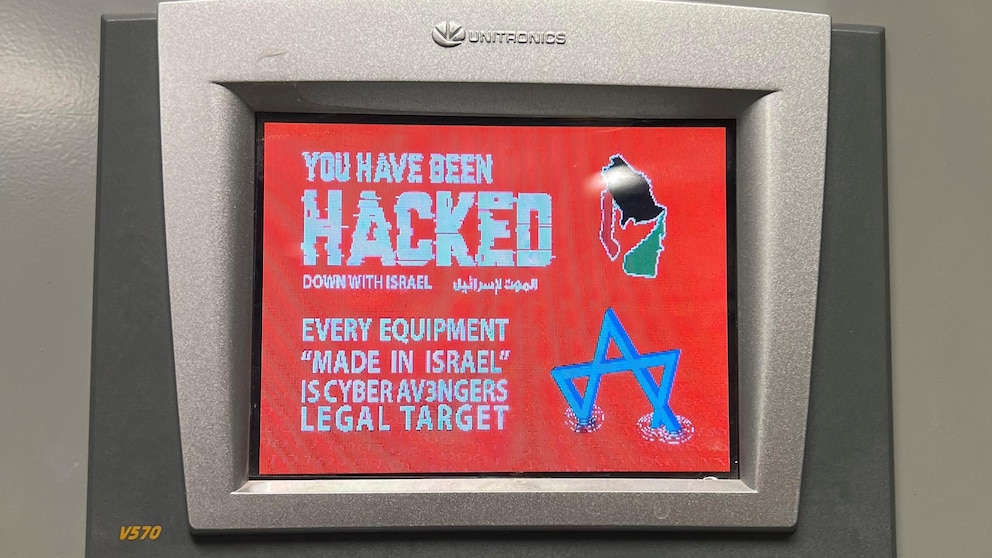
The multiagency advisory explained what CISA had not when it confirmed the Pennsylvania hack on Wednesday — that other industries outside water and water-treatment facilities use the same equipment — Vision Series programmable logic controllers made by Unitronics — and were also potentially vulnerable.
Those industries include “energy, food and beverage manufacturing and healthcare,” the advisory says. The devices regulate processes including pressure, temperature and fluid flow.
The Aliquippa hack promoted workers to temporarily halt pumping in a remote station that regulates water pressure for two nearby towns, leading crews to switch to manual operation. The hackers left a digital calling card on the compromised device saying all Israeli-made equipment is “a legal target.”
The multiagency advisory said it was not known if the hackers had tried to penetrate deeper into breached networks. The access they did get enabled “more profound cyber physical effects on processes and equipment,” it said.
Source…