How the FBI goes after DDoS cyberattackers
Image Credits: TechCrunch (via PhotoMosh)
In 2016, hackers using a network of compromised internet-connected devices — vulnerable security cameras and routers — knocked some of the then biggest websites on the internet offline for several hours. Twitter, Reddit, GitHub and Spotify all went down intermittently that day, victims of what was at the time one of the largest distributed denial-of-service attacks in history.
DDoS is a form of cyberattack where bad actors flood websites with malicious traffic with the goal of taking them offline. DDoS attacks had existed for years before 2016, but the fact that this one incident took down so many major services drew the attention of people who didn’t know much about cybersecurity.
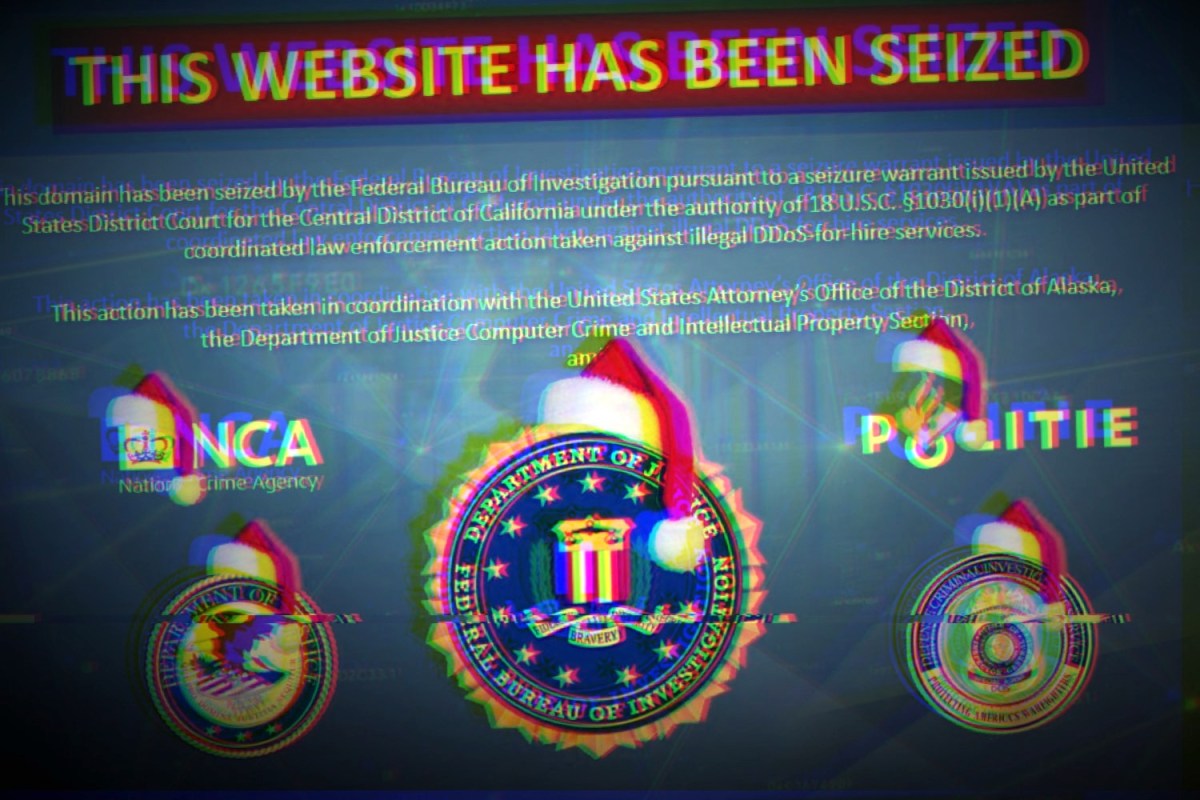
Since then, no DDoS attack has ever been so newsworthy, but the problem hasn’t gotten away. On December 15, 2022, right before Christmas — historically a popular time to launch DDoS attacks — the FBI announced that it had taken down dozens of websites that sell what are called booter or stressers, essentially DDoS-for-hire services. These are relatively cheap services that allow people with low or no hacking skills to carry out DDoS attacks.
On the same day, the feds also announced that they had arrested seven people who allegedly ran those services. Then, the FBI targeted those services and took down more booter sites in May.
All these recent operations — as well as the investigation into Mirai, the malware used in the infamous 2016 attacks — were led by the FBI office in Anchorage.
On Wednesday, Elliott Peterson, one of the FBI agents who led those investigations, spoke at the Black Hat cybersecurity conference in Las Vegas. Peterson, along with Cameron Schroeder, a prosecutor who specializes in cybercrimes, talked about the work behind the investigations that led to the Christmas and May takedowns.
Schroeder also revealed that it was Peterson himself who created the splash pages that replaced the seized websites.
Peterson, who has focused on DDoS attacks for a decade, sat down with TechCrunch on Thursday to talk about his work going after the people behind those DDoS services, and identifying which services to take down. He…