Intel insiders go undercover revealing fresh details into NoName hacktivist operations
In a Black Hat exclusive interview with Cybernews, two Radware threat researchers turned ‘undercover hacktivists’ pose as pro-Russian sympathizers, revealing new insights into the inner workings of the cyberterrorist gang NoName057(16).
“The importance of NoName for us, if you look at the number of attacks that their doing, it’s much bigger than, for example, Anonymous Sudan or even Killnet,” said the Radware researchers, who asked to remain anonymous for security reasons.
Calling Killnet media savvy, the researchers pointed out that “Killnet makes it a lot into the news, but actually, in terms of attacks and targeting, they don’t do that much anymore.”
Anonymous Sudan and Killnet, whose self-proclaimed leader is known as Killmilk, are just two of the well-known pro-Russian hacktivist groups that have been actively targeting Ukraine and the West since the Russian invasion last spring
–
but more on that later.
The two unnamed insiders sat down with me to tell their tale on the last day of the Black Hat USA convention, settling in at a random table on the floor of the swag-filled Business Hall, away from the commotion.
Cybernews readers will get to see the visuals accompanying their research – For Intel and Profit: Exploring the Russian Hacktivist Community – here for the first time.
From insights into the ever-evolving Russian hacktivist landscape to documenting NoName’s steady stream of persistent attacks, these security gurus have proven firsthand that the gang’s crowdsourced “DDoSia” platform is providing a steady stream of crypto payouts to otherwise ordinary citizens whose only commonality is that they despise Ukraine and any of its Western supporters.
Furthermore, according to the duo, it’s not going to stop anytime soon.
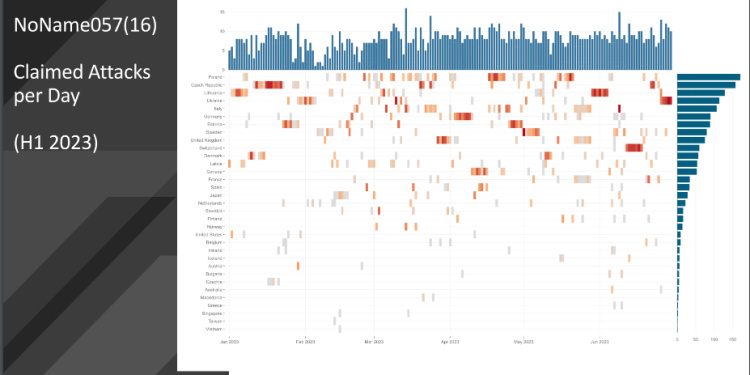
Who is NoName057(16)?
Before we dive right into the gang’s newly discovered operations, let’s briefly profile this steadfast group of attackers and find out what they’ve been up to since they first entered the scene back in March of 2022, and more recently.
To begin with, Radware’s research shows that NoName dominated the pro-Russian hacktivist landscape in the first half of 2023, carrying out a whopping 1174…


