Israel-based Spyware Firm QuaDream Targets High-Risk iPhones with Zero-Click Exploit
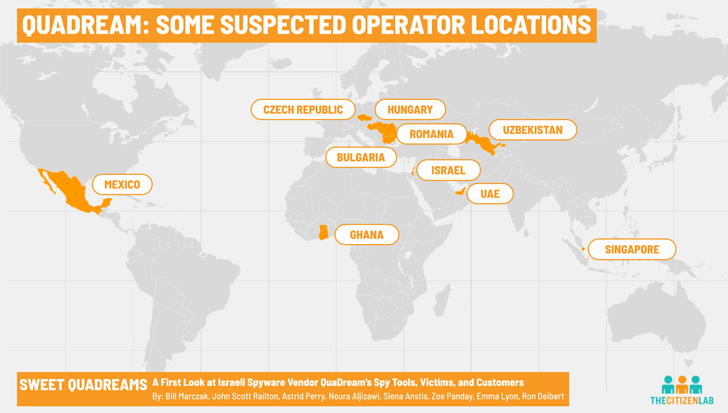
Threat actors using hacking tools from an Israeli surveillanceware vendor named QuaDream targeted at least five members of civil society in North America, Central Asia, Southeast Asia, Europe, and the Middle East.
According to findings from a group of researchers from the Citizen Lab, the spyware campaign was directed against journalists, political opposition figures, and an NGO worker in 2021. The names of the victims were not disclosed.
It’s also suspected that the company abused a zero-click exploit dubbed ENDOFDAYS in iOS 14 to deploy spyware as a zero-day in version 14.4 and 14.4.2. There is no evidence that the exploit has been used after November 2021.
ENDOFDAYS “appears to make use of invisible iCloud calendar invitations sent from the spyware’s operator to victims,” the researchers said, adding the .ics files contain invites to two backdated and overlapping events so as to not alert the users.
The attacks are suspected to have leveraged a quirk in iOS 14 that any iCloud calendar invitation with a backdated time received by the phone is automatically processed and added to the users’ calendar without any notification or prompt.
The Microsoft Threat Intelligence team is tracking QuaDream as DEV-0196, describing it as a private sector offensive actor (PSOA). While the cyber mercenary company is not directly involved in targeting, it is known to sell its “exploitation services and malware” to government customers, the tech giant assessed with high confidence.
The malware, named KingsPawn, contains a monitor agent and the primary malware agent, both of which are Mach-O files written in Objective-C and Go, respectively.
While the monitor agent is responsible for reducing the forensic footprint of the malware to evade detection, the main agent comes with capabilities to gather device information, cellular and Wi-Fi data, harvest files, access camera in the background, access location, call logs, and iOS Keychain, and even generate an iCloud time-based one-time password (TOTP).
Other samples support recording audio from phone calls and the microphone, running queries in SQL databases, and cleaning up forensic trails, such as deleting all calendar events from two years prior…