North Korean Hackers Found Behind a Range of Credential Theft Campaigns
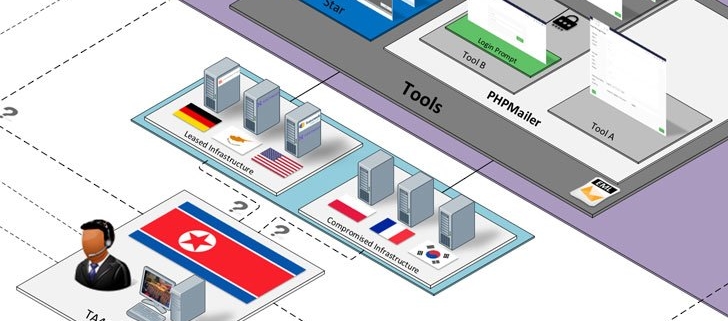
A threat actor with ties to North Korea has been linked to a prolific wave of credential theft campaigns targeting research, education, government, media and other organizations, with two of the attacks also attempting to distribute malware that could be used for intelligence gathering.
Enterprise security firm Proofpoint attributed the infiltrations to a group it tracks as TA406, and by the wider threat intelligence community under the monikers Kimsuky (Kaspersky), Velvet Chollima (CrowdStrike), Thallium (Microsoft), Black Banshee (PwC), ITG16 (IBM), and the Konni Group (Cisco Talos).
Policy experts, journalists and nongovernmental organizations (NGOs) were targeted as part of weekly campaigns observed between from January through June 2021, Proofpoint researchers Darien Huss and Selena Larson disclosed in a technical report detailing the actor’s tactics, techniques, and procedures (TTPs), with the attacks spread across North America, Russia, China, and South Korea.
Known to be operational as early as 2012, Kimsuky has since emerged as one of the most active advanced persistent threat (APT) group known for setting its sights on cyber espionage but also for conducting attacks for financial gain, targeting government entities, think tanks, and individuals identified as experts in various fields as well as harvest sensitive information pertaining to foreign policy and national security issues.
“Like other APT groups that constitute a big umbrella, Kimsuky contains several clusters: BabyShark, AppleSeed, Flower Power, and Gold Dragon,” Kaspersky researchers noted in their Q2 2021 APT trends report published last month. The AppleSeed sub-group is also referred to as TA408.
The group is also known for reeling in targets with convincing social engineering schemes and watering hole attacks before sending them malware-infected payloads or tricking them into submitting sensitive credentials to phishing sites, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said in a public alert issued in October 2020.
Earlier this month, researchers from Cisco Talos disclosed an ongoing Kimsuky campaign since June 2021 that was found leveraging malicious blogs hosted on Google’s…