Out of the blue: Surviving an 18-hour, 39M-request DDoS attack
No online business can afford to neglect malicious bot threats. Attackers and fraudsters increasingly leverage bots to automate and coordinate attacks, driving IT teams and ill-equipped security tools to their limits.

Only a full-endpoint, 360° bot protection solution that leverages aggregate global detection signals can save you from unexpected threats.
Case in point: A large e-commerce website protected by DataDome’s bot and online fraud management solution recently remained blissfully unaffected throughout a high volume, highly-distributed DDoS attack. What’s more, the site implemented the protection to solve a scraping problem.
Let’s deep dive into a real-life attack to understand the key traits of a DDoS attack, how the threat landscape is evolving, and the implications when choosing a security solution.
The attack, as it happened
Beginning on a Friday and lasting through Saturday, the DDoS attack came in several waves spanning over 18 hours. In total, the site was under active attack for ~4 hours.
The attack can be split into two main waves:
- 1st wave: Friday night between ~18:00 and ~0:00 (CEST).
- 2nd wave: Saturday morning from ~10:00 to 12:00.
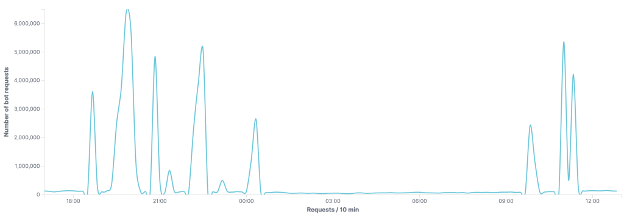
The first part of the attack represented the highest volume of traffic (29.375 million bot requests). During this first wave, the DDoS generated spikes of traffic that reached up to 1.5 million requests per minute.
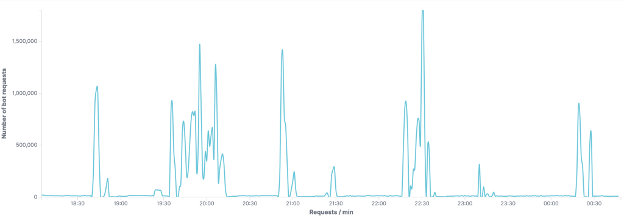
The attack, like most DDoS attacks these days, was heavily distributed. The attacker leveraged a botnet of more than 11,000 distinct IP addresses from 1,500 different autonomous systems, spread over 138 countries.
The point: Simple IP rate limiting or geo-blocking would not have been effective.
The targeted website has customers all around the world. So, while blocking all requests from certain countries could have helped mitigate the attack, it would have also impacted the user experience for innocent customers based in the blocked countries.
If we look at the distinct number of IP addresses used by the botnet in the timeline, we see that during each spike, the botnet was making requests from more than 5,000 different IP addresses.
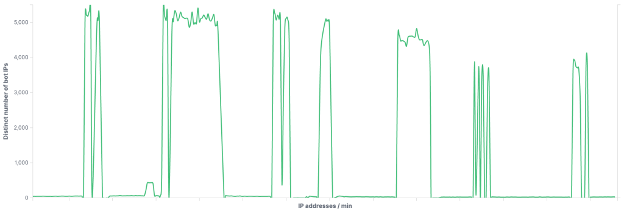
Requests came from all around the world, in particular from the US…


