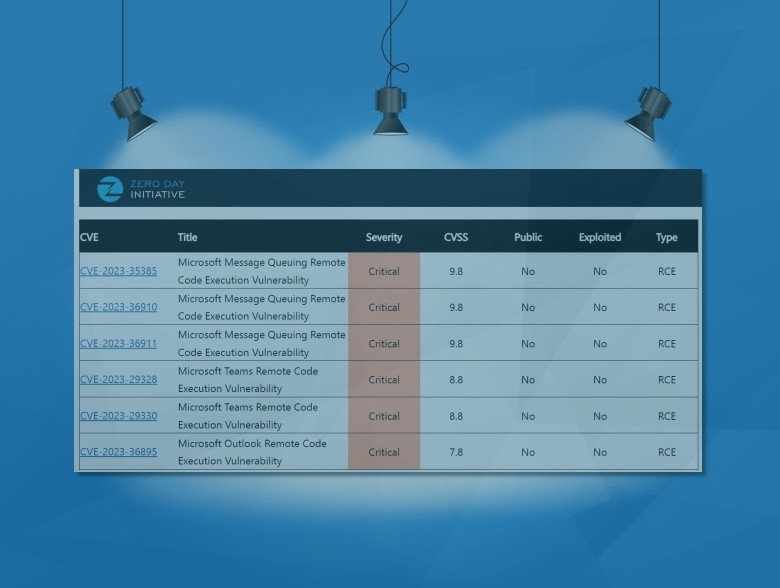
Publisher’s Spotlight: The Zero Day Initiative (ZDI): Financially Rewarding InfoSec Researchers
Formed by TrendMicro, the Zero Day Initiative (ZDI) was created to encourage the reporting of 0-day vulnerabilities privately to the affected vendors by financially rewarding researchers. At the time, there was a perception by some in the information security industry that those who find vulnerabilities are malicious hackers looking to do harm. Some still feel that way. While skilled, malicious attackers do exist, they remain a small minority of the total number of people who discover new flaws in software.
Incorporating the global community of independent researchers also augments their internal research organizations with the additional zero-day research and exploit intelligence. This approach coalesced with the formation of the ZDI, launched on July 25, 2005.
Today, the ZDI represents the world’s largest vendor-agnostic bug bounty program. Their approach to the acquisition of vulnerability information is different than other programs. No technical details concerning the vulnerability are sent out publicly until the vendor has released a patch.
One of their cool events is Pwn2Own, held in multiple countries – here’s their recent scoreboard from their Vancouver, Canada event:
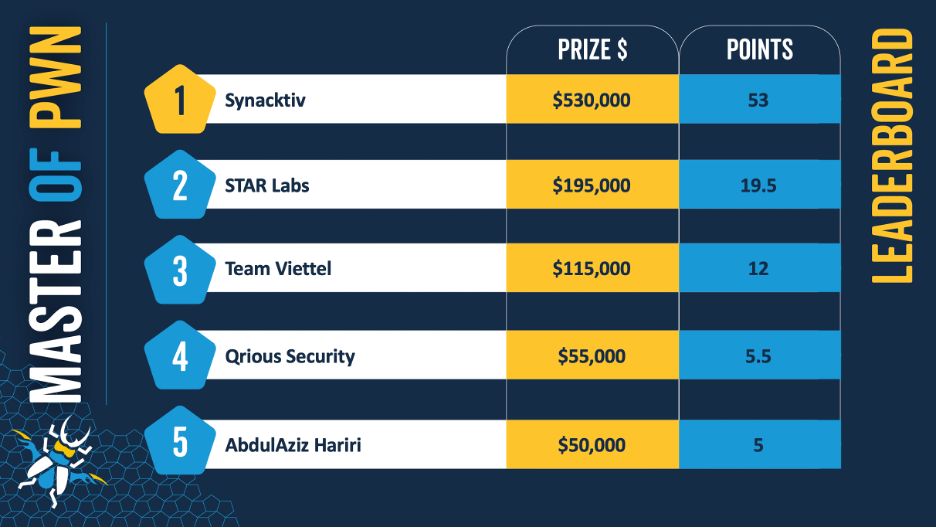
Contestants disclosed 27 unique zero-days and won a combined $1,035,000 (and a car)! Congratulations to the Masters of Pwn, Synacktiv (@Synacktiv), for their huge success and hard work! They earned 53 points, $530,000, and a Tesla Model 3:

They do not resell or redistribute the vulnerabilities that are acquired through the ZDI. Submitting through the ZDI program also relieves you from the burden of tracking the bug with the vendor. They make every effort to work with vendors to ensure they understand the technical details and severity of a reported security flaw, which leaves researchers free to go find other bugs. They will let you know where things stand with all your own current cases with regards to vendor disclosure. In no cases will an acquired vulnerability be “kept quiet” because a product vendor does not wish to address it.
Interested researchers provide them with exclusive information about previously un-patched vulnerabilities they have discovered. The ZDI then collects…