Ransomware Operators Using SystemBC Malware as Backdoor
Fraud Management & Cybercrime
,
Next-Generation Technologies & Secure Development
,
Ransomware
Researchers Have Seen Commodity Malware Used With Ryuk and Egregor
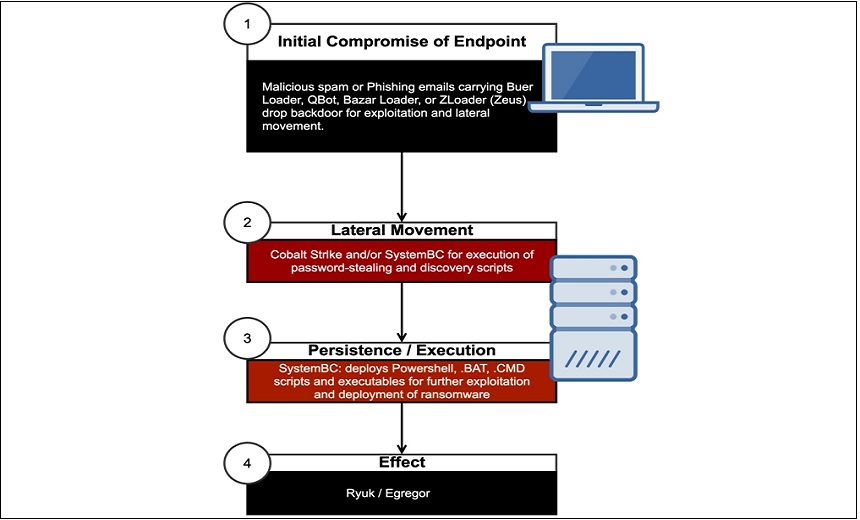
Several recent ransomware attacks, including those involving Ryuk and Egregor, have used a commodity malware variant called SystemBC as a backdoor, security firm Sophos reports.
See Also: 7 Ways to Take Cybersecurity to New Levels
First uncovered by security firm Proofpoint in August 2019, SystemBC works as a network proxy for concealed communications as well as remote access Trojan, or RAT, that allows threat actors to deploy additional commands and scripts to infected Windows devices as well to gather data.
And while researchers have tracked SystemBC over the years, the Sophos report finds that its creators have added new features, with ransomware operators and their affiliates taking advantage of these updates to deploy their crypto-locking malware.
Sophos found that the SystemBC malware now uses the Tor anonymizing network to encrypt and conceal the destination of command-and-control server traffic. This not only helps obfuscate the attackers’ communications but also allows them to better hide when data is gathered and exfiltrated, according to the report.
“Collectively, these capabilities give attackers a point-and-shoot capability to perform discovery, exfiltration and lateral movement with packaged scripts and executables – without having to have hands on keyboard,” Sophos analysts…


