CL0P Ransomware Activity Heats Up
Ransomware activity from cybercriminal group CL0P increased massively in April over March this year, a new report by cybersecurity consultant NCC Group found. The number of CL0P’s victims increased from just one in March to 21 in April.
The April Threat Pulse research report notes that CL0P exhibited an explosive return to the ransomware threat landscape, pushing them from the least active criminal group in March to the fourth most prominent in April. NCC Group’s threat intelligence team says CL0P’s presence has been extremely volatile throughout 2022 thus far – from zero attacks in January, to 10 in February, one in March, and 21 in April.
A similar fluctuation in the rate of the group’s attacks was also seen across 2021, so the April uptick doesn’t necessarily indicate a marked comeback for CL0P. Rather, April was an “active month” for the group, the threat intelligence team noted.
REvil Reemerges
Following a quiet period, April also saw the return of threat actor REvil. Responsible for several high-profile disruptive ransomware campaigns in 2021, including the attacks on the Colonial Pipeline and Kaseya, REvil became the focal point for international law enforcement last year. The group’s online infrastructure was disabled, and multiple arrests were made.
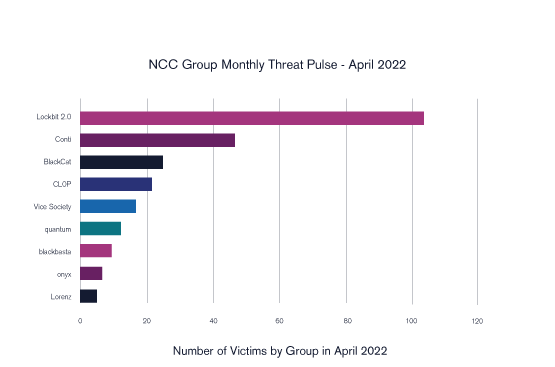
Number of victims by threat actor group in April 2022.
In April, NCC Group threat intelligence saw new activity from REvil, albeit on a small scale with a total of five incidents reported. Each victim came from a different sector, revealing a diverse interest in targeting behavior.
NCC Group notes this return supports the notion that any absence from a ransomware group doesn’t signify a total hiatus in criminal activity, certainly where groups come under the law enforcement firing line, taking cover before regaining momentum.
Conti Group Cools Down
Other criminal groups decreased ransomware activity in April.
After a 115% increase between February and March, NCC Group researchers witnessed a 37% decrease in victims of criminal group Conti from March to April. This volatility may be…





