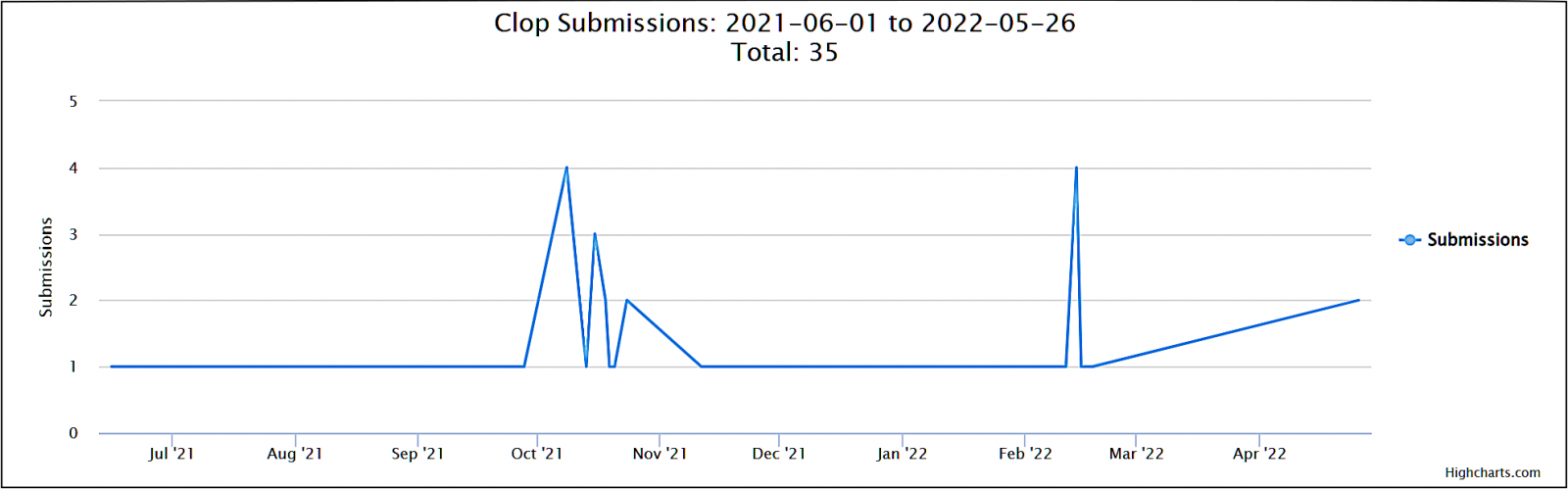
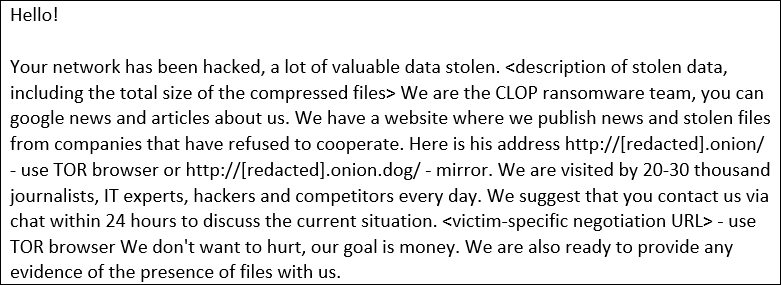
National Critical Infrastructure Under Attack: Clop Ransomware

On August 15, 2022, a U.K. water supplier suffered disrupted essential services within their corporate IT systems. The hackers used a remote access software platform that had been dormant for months.
This is another NCI nation-state ransomware attack.
The recent criminal cyber activity on the IT infrastructure on Monday caused a U.K. water supplier to experience a disturbance in its corporate IT systems. The company insists that its water delivery was unaffected. The UK water company confirmed they activated their continuity of operations plan and cybersecurity response plan, along with notifying the United Kingdom’s legal authorities.
According to a report on Bleepingcomputer, the Clop ransomware gang claimed responsibility for an attack on a U.K. water company. The cybercriminals claim the Thames Water and not South Staffordshire was the target. The fallout from the cyber attack against the UK water system
The SCADA systems were allegedly breached by the Clop ransomware, which threatened to harm the consumers of the UK water supply. Despite not encrypting the PCs of its victims, the gang claims to have accessed 5 Terabytes of data during the attack. Even with several layers of critical infrastructure controls, this type of activity continues to be a global problem, not just in the UK.
Clop is a ransomware variant of the CryptoMix developed in Russia. Clop employs several strategies to evade discovery and prevent analysis. To prevent the file from executing if it detects that it is running in an emulated environment, the virus uses anti-analysis and anti-virtual machine (VM) tactics. Additionally, the ransomware tries to deactivate Windows Defender and remove Microsoft Security Essentials.
As Industrial systems connect with the internet to leverage cloud analytics, the devices have become more vulnerable to cyberattacks. Industrial control systems (ICS) and the internet of things (IoT) are specifically vulnerable to cyber threats because of improper OT security systems and vulnerabilities within the product.
During production, critical infrastructure equipment such as intelligent building control systems, fire and safety systems, traffic control systems, intelligent…