Ransomware and Darknet Markets Top List For Most Prominent Crypto Crimes

A new report from blockchain analysis firm Chainalysis found that crypto related crimes decreased in 2023. While notable, findings also show that ransomware and darknet market activity involving cryptocurrency increased considerably.
Eric Jardine, cybercrime research lead for Chainalysis, told Cryptonews that both ransomware wallets and darknet market wallets saw more inflows during 2023 than 2022 measured in terms of dollars. Jardine further explained that these two categories of illicit activity involve different underlying patterns of behavior. He said:
“In the case of ransomware, for example, increased inflows mean that individuals, companies, critical infrastructure providers, and governments are paying more or larger ransoms after being the victim of a cyberattack by a malicious actor in 2023 than they did in 2022. In the case of darknet markets, inflows often represent various forms of illegal activity, most notably the purchase of illicit drugs such as fentanyl, heroin, or cocaine.”
Why ransomware and darknet market activities are increasing
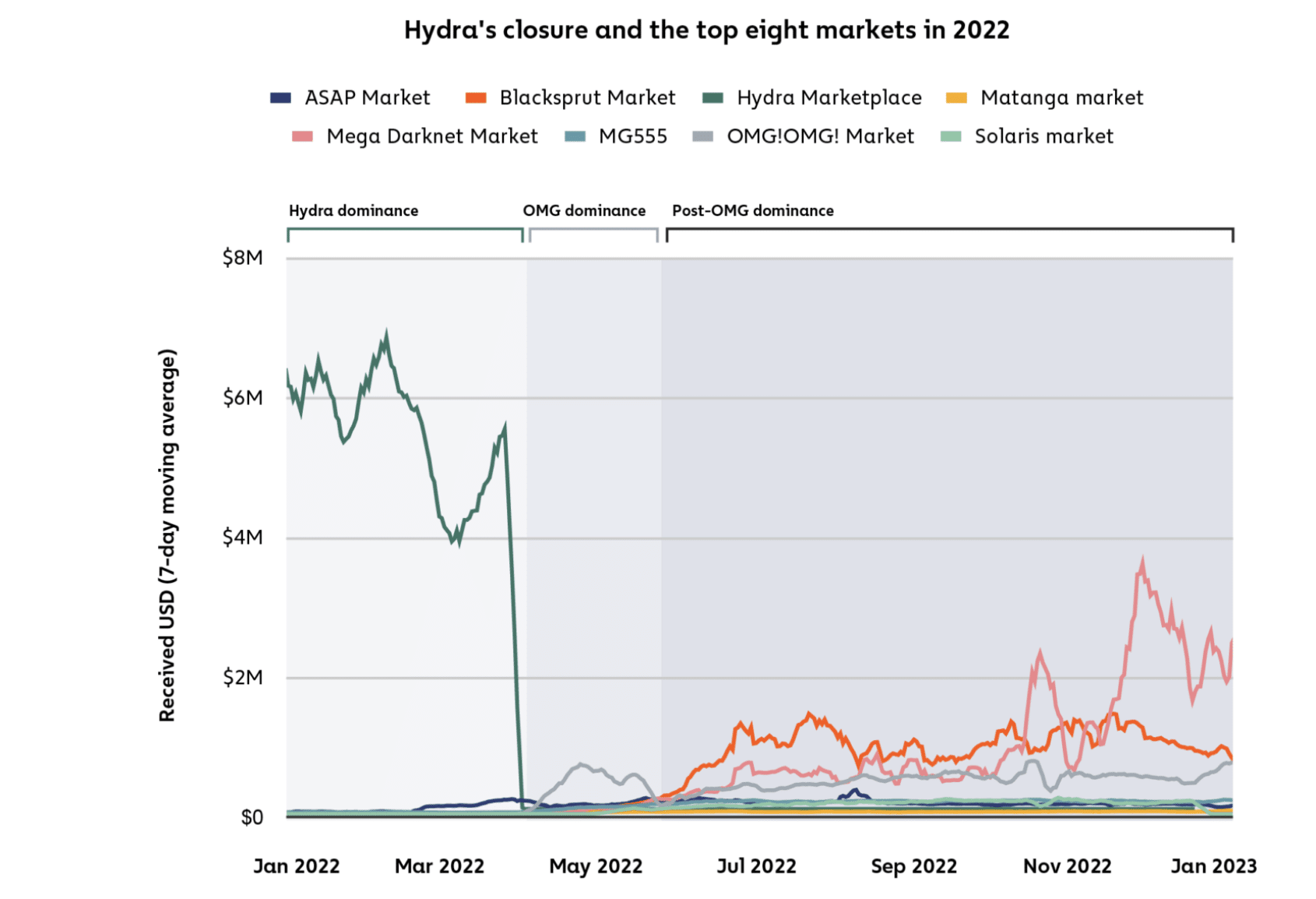
Unfortunately, Jardine believes that 2023 marked the recovery of the illicit darknet ecosystem. He mentioned that the closure of Hydra Marketplace in 2022 – one of the largest darknet marketplaces – reduced the aggregate inflows to darknet markets that year. However, this also resulted in an influx in darknet market activity during 2023.