Oakley, Pleasant Hill face cyber incidents
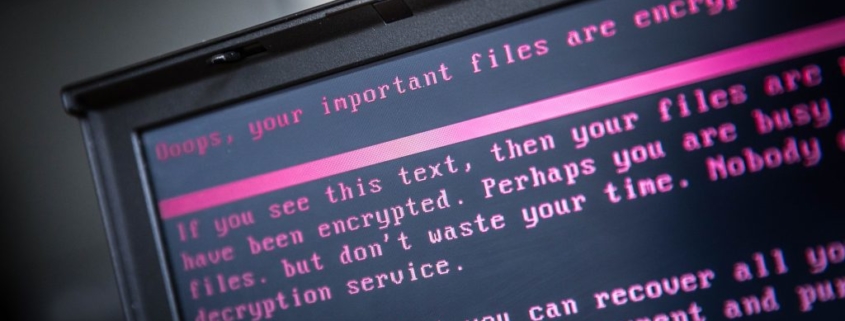
A laptop displays a message after being infected by a ransomware as part of a worldwide cyberattack on June 27, 2017 in Geldrop.
The unprecedented global ransomware cyberattack has hit more than 200,000 victims in more than 150 countries, Europol executive director Rob Wainwright said May 14, 2017. Britain’s state-run National Health Service was affected by the attack. / AFP PHOTO / ANP / Rob Engelaar / Netherlands OUT (Photo credit should read ROB ENGELAAR/AFP/Getty Images)
The cities of Pleasant Hill and Oakley both experienced cyber security incidents on Thursday.
Officials from the city of Pleasant Hill said Friday that their IT professionals detected a cyber intrusion that targeted the city’s computer servers Thursday afternoon and responded quickly to isolate the threat, but they don’t yet know the extent of the intrusion. The Pleasant Hill Police Department is investigating the incident.
The city of Oakley was also hit Thursday afternoon. In response to a ransomware attack, the Oakley city manager declared a local state of emergency.
Oakley’s IT department has taken affected systems offline and is coordinating with law enforcement and cybersecurity professionals to investigate how severe the problem is, according to the city. While emergency services are not impacted, people should expect delays for non-emergency city services.
“We are actively monitoring the situation and will provide updated information as it becomes available,” city officials said in a statement.
View more on
The Mercury News