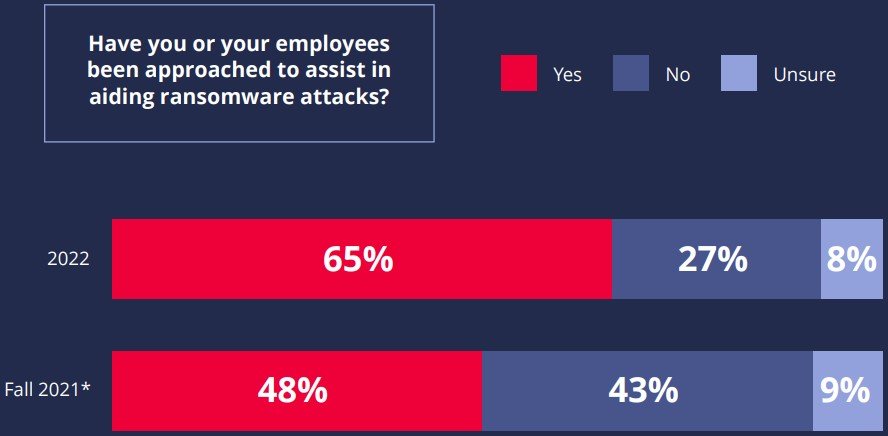
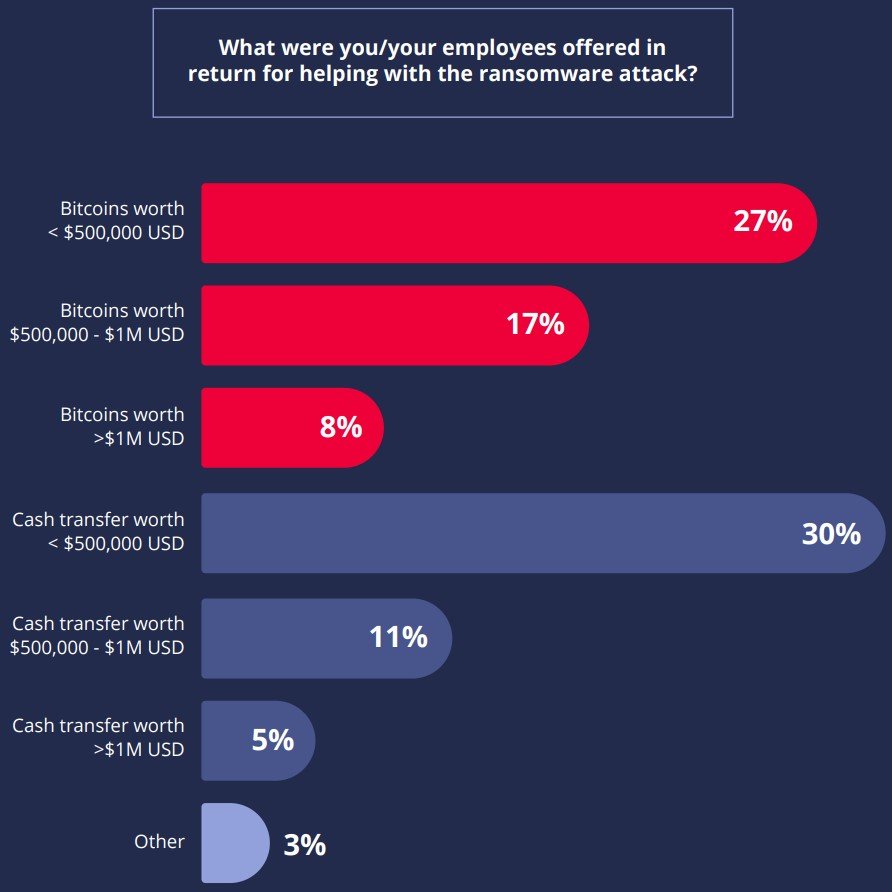
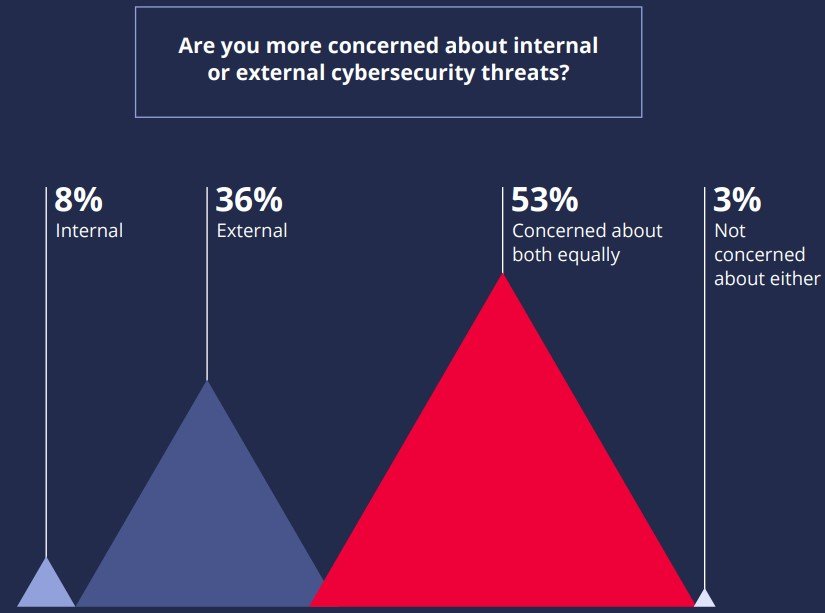
Ransomware gangs are hitting roadblocks, but aren’t stopping (yet)
Ransomware attacks are in decline, according to reports by several cybersecurity companies. Why is that?
More effort for less pay
In its mid-year 2022 Cyber Threat Report, SonicWall notes that there has been a global 23% drop in ransomware, “as geopolitical forces, volatile cryptocurrency prices, and increased government and law-enforcement focus impacted both who cybercriminals chose to attack and how well they were capable of carrying out those attacks.”
After witnessing many high-profile destructive attacks, companies have also been hardening their defenses, putting another obstacle in front of ransomware groups.
Among the reasons for the decline could also be that fewer organizations are willing to pay a ransom: According to Coveware, in Q1 of 2019, 85% of the cases they handled ended in the cyber criminal receiving a ransom payment, and in Q1 2022 that percentage fell down to 46%.
In Q2 2022, the median ransom payment also went down by 51% from Q1 2022.
“This trend reflects the shift of RaaS affiliates and developers towards the mid market where the risk to reward profile of attack is more consistent and less risky than high profile attacks. We have also seen an encouraging trend among large organizations refusing to consider negotiations when ransomware groups demand impossibly high ransom amounts,” the company shared.
To pay or not to pay?
Two US states (North Carolina and Florida) recently prohibited state agencies, counties and minicipalities from paying a ransom in response to a ransomware incident. North Carolina’s prohibition even extends to public schools and universities. BakerHostetler counsel Benjamin Wanger and associate Elise Elam say that they “expect to see similar laws introduced and/or passed in several additional states.”
Whether that’s a good move remains to be seen, but even IBM Security’s 2022 Cost of a Data Breach Report notes that, oftentimes, it doesn’t pay to pay the ransom.
“Ransomware victims in the study that opted to pay threat actors’ ransom demands saw only $610,000 less in average breach costs compared to those that chose not to pay – not including the cost of the ransom. Factoring in the high cost of ransom…