Beating the bad bots: Six ways to identify and block spam traffic
Advancements in technology have helped us propel forward, changing the way we work and live our daily lives. However, its rapid adoption has led to less sombre means. We have all seen and participated in those various bot tests that some websites carry out, where we have to select the picture tiles which have particular objects. This is to control the usage of the site and reduce spam traffic.
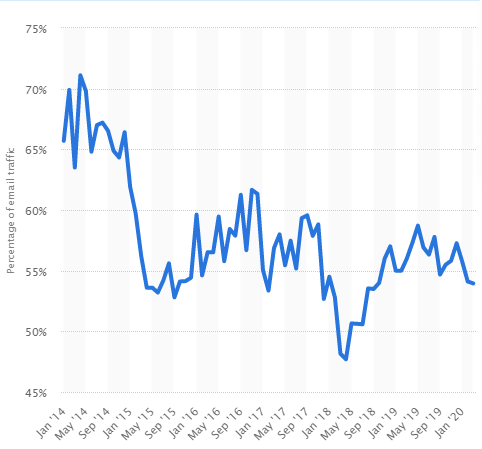
Spam traffic is used in some cases by cybercriminals to commit scams and fraud and has become a tool for phishing scam and malware spread. It is problematic as it is inexpensive to create and send. In 2020, spam messages accounted for a colossal 58.71 percent of email traffic as the graph above indicates.
What is a bad bot?
There are a range of different bots that you find on the backend of the internet carrying out different types of tasks. Some are harmless such as search engine bots used by Google and Bing, which help the service specifically by browsing the internet to help make available content that can be useful to users based on search queries.
However, bad bots are used in an entirely different way to serve a different purpose. These include. Searching sites and scraping data of it to benefit other sites or sell on and steal information and repost it under a different identity.
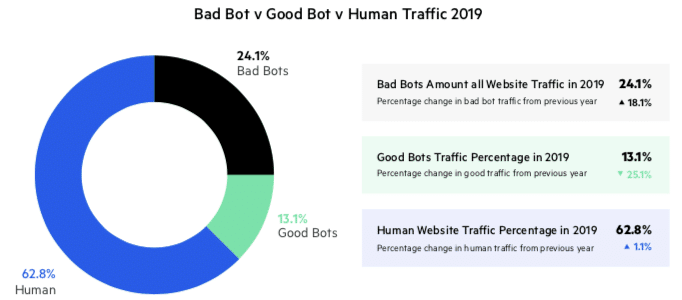
Bad bots also can disturb site metrics as they inflate search results and increase website traffic unnecessarily, leading to slower loading times and unnecessary investments in hardware to maintain the website infrastructure. As we can see from the graph below, in 2019, 24 percent of traffic emanated from the movement of bad bots.
They are also able to perform malicious acts on-site, which lead to damaging networks through things such as distributed denial of service (DDoS) attacks. These attacks flood sites with data higher than a level that it can handle.
Bad bots are mostly organized on botnets which are a collection of internet-connected devices that have been infected by malware, allowing hackers to control them. Cybercriminals use botnets to instigate a botnet attack, and these attacks consist of malicious activities.
Attacks such as these are hard to prevent as they can come in many shapes and forms as…