Hunters International Ransomware Adds Four New Victims
The Hunters International ransomware group has claimed four new victims, expanding its reach across industries and countries.
The targeted organizations include Gunning & LaFazia in the United States, Thermosash Commercial Limited in New Zealand, PROJECT M.O.R.E. in the U.S., and Bradford Health Care, a healthcare institution.
The Targets: Diverse Industries and Geographic Locations
The announcement of cyberattack was made through the group’s dark web portal, showcasing their continued audacity in breaching security systems. The implications of these Hunters International ransomware attacks could be far-reaching, given the diverse industries and geographic locations of the victims.
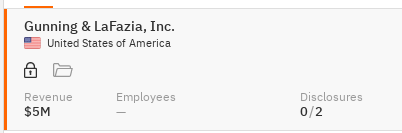
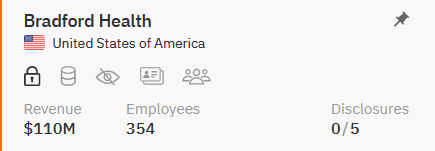
The USA and New Zealand have found themselves at the forefront of this latest cyber onslaught.


To verify the legitimacy of the Hunters International ransomware attack claim, The Cyber Express Team reached out to the targeted organizations. Unfortunately, as of the writing of this report, no responses have been received, leaving the claims unverified.
Interestingly, the official websites of the targeted organizations were found to be fully functional, raising questions about the authenticity of the Hunters International ransomware group’s assertions.
Hunters International ransomware has become synonymous with a repetitive attack pattern, drawing parallels to their previous operations. A significant revelation from October exposed code overlaps between the ransomware used by Hunters International and the once-dominant Hive ransomware.
Bitdefender, a cybersecurity vendor, confirmed this finding, suggesting a strategic decision by the Hive group to transfer its operations and assets to Hunters International.
Repetitive Tactics: Hunters International Ransomware Attack Pattern
This recent cyberattack on multiple organizations echoes a similar pattern observed in 2023 when the L’Azienda USL di Modena Regional Health Service in Italy fell victim to a cyber breach attributed to Hunters International.
Before these incidents, the ransomware group targeted InstantWhip, a major player with a revenue of US$300 million. InstantWhip has yet to release any…