La Botnet Mirai IZ1H9 amplia il suo arsenale. 13 nuovi exploit per dispositivi IoT sono stati integrati

La Botnet Mirai IZ1H9 amplia il suo arsenale. 13 nuovi exploit per dispositivi IoT sono stati integrati
Redazione RHC 12 Ottobre 2023 08:28
La botnet, che i ricercatori rintracciano con l’identificatore IZ1H9, ha recentemente acquisito tredici nuovi exploit per attaccare router Linux, nonché dispositivi di D-Link, Zyxel, TP-Link, TOTOLINK e altri produttori.
Questa variante di Mirai è stata scoperta per la prima volta nell’agosto 2018 ed è una delle più attive: sfrutta le vulnerabilità senza patch dei dispositivi IoT per infettarli e utilizzarli per lanciare attacchi DDoS.
Secondo gli esperti di Fortinet, il picco degli attacchi IZ1H9 si è verificato nella prima settimana di settembre, quando il numero di tentativi di hacking dei dispositivi vulnerabili ha raggiunto le decine di migliaia.
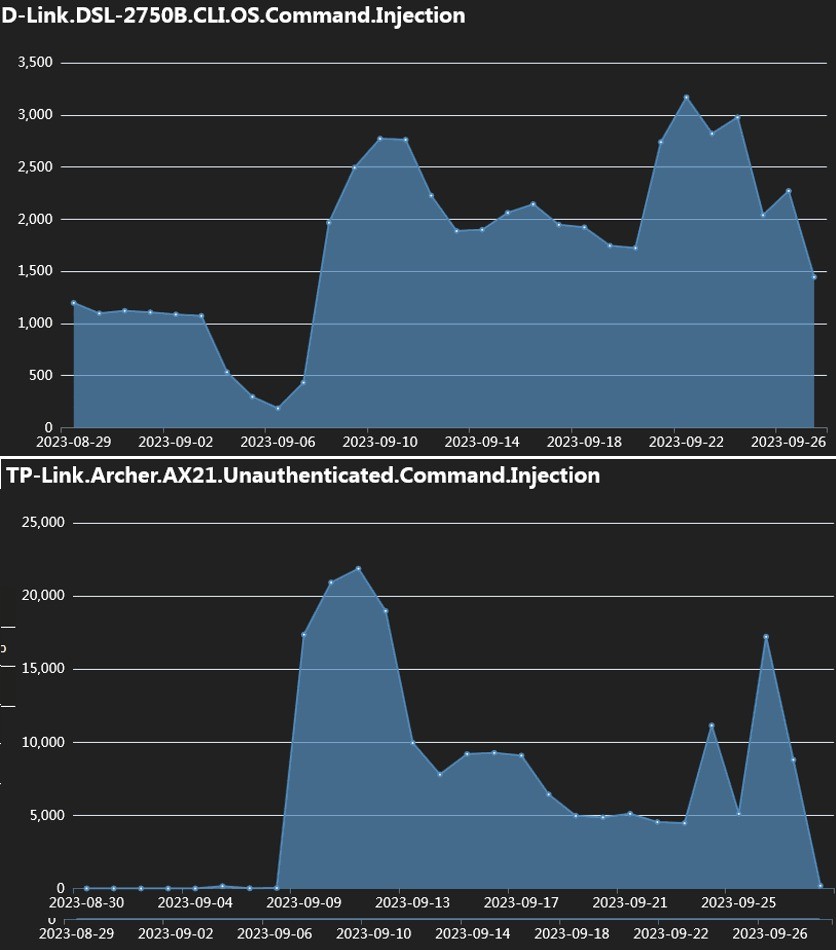
I ricercatori elencano che in totale la botnet IZ1H9 utilizza più di 30 exploit nei suoi attacchi per le seguenti vulnerabilità risalenti al 2013-2015:
- D-Link : CVE-2015-1187, CVE-2016-20017, CVE-2020-25506, CVE-2021-45382;
- Netis WF2419 — CVE-2019-19356;
- Sunhillo SureLine (versioni fino a 8.7.0.1.1) — CVE-2021-36380;
- Geutebruck — CVE-2021-33544, CVE-2021-33548, CVE-2021-33549, CVE-2021-33550, CVE-2021-33551, CVE-2021-33552, CVE-2021-33553, CVE-2021-33554;
- Gestione dispositivi Yealink (DM) 3.6.0.20 — CVE-2021-27561, CVE-2021-27562
- Zyxel EMG3525/VMG1312 (prima della versione 5.50) : nessun CVE, ma esiste una vulnerabilità nel componente /bin/zhttpd/ dei dispositivi Zyxel;
- TP-Link Archer AX21 (AX1800) — CVE-2023-1389;
- Punti di accesso wireless Korenix JetWave – CVE-2023-23295;
- router TOTOLINK — CVE-2022-40475, CVE-2022-25080, CVE-2022-25079, CVE-2022-25081, CVE-2022-25082, CVE-2022-25078, CVE-2022-25084, CVE-2022-2507 7 , CVE-2022-25076, CVE-2022-38511, CVE-2022-25075, CVE-2022-25083;
- Router Prolink PRC2402M – CVE non specificato relativo a /cgi-bin/login.cgi (il payload associato ad esso non funziona).
Una volta sfruttata una delle vulnerabilità elencate, sul dispositivo viene consegnato il payload IZ1H9, che contiene un comando per ottenere il loader di script della shell l.sh da un URL specifico. Una volta eseguito, questo script rimuove i log per nascondere attività dannose e quindi recupera…



