Ransomware attack hits Goa’s flood monitoring system; demand crypto as payment | Latest News India
In a complaint to the cyber cell, the state government’s water resources department that has been maintaining the data said that all its files have been encrypted and can no longer be accessed.
Goa’s flood monitoring system was hit by ransomware attackers who have demanded to be paid in cryptocurrency for the data on flood monitoring stations to be released.
In a complaint to the Cyber cell of the Goa Police, the state government’s water resources department that has been maintaining the data said all its files have been encrypted and can no longer be accessed.
Also Read: A multipronged approach to protect ICT supply chains from cyberattacks
“Server has been under the cyberattack of ransomware. Under the attack, all files are encrypted with eking extension and cannot be accessed. In a popup and stored file, the attackers are demanding Bitcoins Cryptocurrency for the decryption of the data. The attack was carried out on 21 June 2022 midnight between 12am-2am. The integrity of the data has been altered making it impossible to back up the previous data. The server works on the 24×7 internet line and the attack was eased due to absence of antivirus and outdated firewalls,” the complaint filed by executive engineer Sunil Karmarkar revealed.
The complaint was filed on June 24 but has come to light today.
The data center server located at Panaji was storing data of the flood monitoring system at 15 locations on major rivers in Goa to monitor flood levels in rivers as a part of disaster management in order to have a control on floods eventualities.
The data of flood monitoring system, automated rain gauges and weather gauges get stored in the server located at the Water Resources Department Headquarters in the state capital while the servers were being maintained by ASTRA Microwave Products limited, Hyderabad.
As a result of the hacking, the department can now no longer access its data related to battery voltages of different stations, data packets related to 12 stations, has lost all its old data which can now no longer be backed up locally and has also lost real time data of the rivers currently in spate owing to the ongoing vigorous monsoon activity across the state.
Focus on Monitoring, Risk Management, & Access Management

Global Social Media Security Market
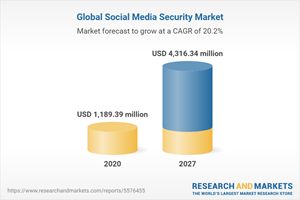
Dublin, May 26, 2022 (GLOBE NEWSWIRE) — The “Social Media Security Market – Forecasts from 2022 to 2027” report has been added to ResearchAndMarkets.com’s offering.
The social media security market is expected to reach a market size worth US$4,316.343 million by 2027, growing at a CAGR of 20.22%. This market was valued at US$1,189.385 million in 2020.
Social media is an emerging platform where people connect for numerous purposes. With rising internet penetration and growing smart device usage, social media is gaining robust popularity and adoption. However, with flourishing social platforms and users, social crime and insecurities have increased tremendously.
Social crime includes social harassment, fake profiles, misguiding leads, data theft, breaching, hacking, and others. The high risk of social crime creates the market demand for social media security services. It is expected that rising instances of social crime and dysfunctions will drive the market demand for social media security. Furthermore, expanding social media platforms’ usage as earning sources has also increased the market prospects for social media security.
Geographically, the social media security market is divided into North America, South America, Europe, the Middle East and Africa, and the Asia Pacific regions for the study. The Asia Pacific social media security market is expected to grow at a lucrative rate during the forecasted period. The regional market is fueled by growing internet penetration in the region and the rising adoption of social media.
Furthermore, an increase in social media earnings has notably increased disposable income. Social media platforms such as Instagram and Facebook have emerged as entertainment, education, skill enhancement, and connection area in the Asia Pacific region, which has significantly surged social media earnings.
A rise in income and propelling threat of social and cybercrime are expected to drive the market for social media security in the region. North America and European regions are anticipated to dominate the market owing to higher expenditure capability and significant users.
Growth…
How to avoid security blind spots when logging and monitoring
Cybersecurity involves a balancing act between risk aversion and risk tolerance. Going too far to either extreme may increase cost and complexity, or worse: cause the inevitable business and compliance consequences of a successful cyberattack. The decisions that need to be made around logging and monitoring are no exception.

Capturing all data from every device on the network can create bottlenecks, overwhelm log management, and obfuscate signs of network penetration, or malicious activity. Not capturing all the critical log data can result in monitoring that fails to identify attacks before they do damage or assist in forensics after the incident.
Getting logging and monitoring right is so important that it is listed among the Center for Internet Security’s critical security controls.
Failing to log creates blind spots
Failing to activate logging creates security blind spots in your network that will only become apparent after the fact (i.e., when an attack is successful). Every component of your extended infrastructure — on premises and remote — should be configured to generate appropriate audit events. These components include operating systems, system utilities, servers, workstations, networking equipment, and security systems (which include anti-malware, firewalls, intrusion detection and prevention systems, and VPNs).
This applies whether you run your own security information and event management (SIEM) solution for log management or use a managed SIEM with SOC-as-a-Service for 24/7 monitoring, alerting, and reporting. The SIEM relies on log data feeds to provide protection. It can’t see alerts on what’s not being logged. Responsibility for making devices and apps visible often falls outside of the security organization.
For example, failure to activate logging can happen if there is a “set it and forget it” mindset. The reality is that networks are always changing. New endpoint devices are continually being added and removed due to personnel changes, addition of new locations, flexible work programs that let employees work from home, new mobility solutions, and the like.
Assuming that new apps and devices — including new cloud infrastructure…
Catchpoint launches new user experience monitoring platform

Observability company Catchpoint has announced its newest user experience monitoring platform, Catchpoint Symphony.
This new platform was designed based on input from hundreds of users and usability studies. According to Catchpoint, Symphony is intuitive to use, which makes it easy to get started with. It provides a common toolset with simplified workloads.
Customers can use it to perform advanced testing and monitoring, and analyze and correlate broader data sets.
This will allow them to visualize user experience, service, application, and network performance across data sources like real user monitoring data, BGP and network data, and user sentiment and proactive tests.
According to tests by the company, Catchpoint Symphony outperforms other UX systems by 83%. Issues can be identified within 10 seconds using the platform.
“Enterprises increasingly rely on public infrastructure to deliver services and reach users globally – commercial Internet, multi-access edge computing (MEC), multi-CDNs, Internet security, hybrid-cloud, and SaaS” said Mehdi Daoudi, CEO at Catchpoint. “Although the business benefits of leveraging public infrastructure are tremendous, it introduces a lot of complexity and dangerous blind spots, leaving our customers vulnerable to business impacting outages. It also makes it harder to identify and troubleshoot issues proactively before they impact digital user experience. With Symphony and the Catchpoint platform, our customers can remove the inherit public infrastructure blind spots and can identify and fix problems faster than before.”



