The Emotet malware is now being leveraged by ransomware-as-a-service (RaaS) groups, including Quantum and BlackCat, after Conti’s official retirement from the threat landscape this year.
Emotet started off as a banking trojan in 2014, but updates added to it over time have transformed the malware into a highly potent threat that’s capable of downloading other payloads onto the victim’s machine, which would allow the attacker to control it remotely.
Although the infrastructure associated with the invasive malware loader was taken down as part of a law enforcement effort in January 2021, the Conti ransomware cartel is said to have played an instrumental role in its comeback late last year.
“From November 2021 to Conti’s dissolution in June 2022, Emotet was an exclusive Conti ransomware tool, however, the Emotet infection chain is currently attributed to Quantum and BlackCat,” AdvIntel said in an advisory published last week.
Typical attack sequences entail the use of Emotet (aka SpmTools) as an initial access vector to drop Cobalt Strike, which then is used as a post-exploitation tool for ransomware operations.
The notorious Conti ransomware gang may have dissolved, but several of its members remain as active as ever either as part of other ransomware crews like BlackCat and Hive or as independent groups focused on data extortion and other criminal endeavors.
Quantum is also a Conti spin-off group that, in the intervening months, has resorted to the technique of call-back phishing – dubbed BazaCall or BazarCall – as a means to breach targeted networks.
“Conti affiliates use a variety of initial access vectors including phishing, compromised credentials, malware distribution, and exploiting vulnerabilities,” Recorded Future noted in a report published last month.
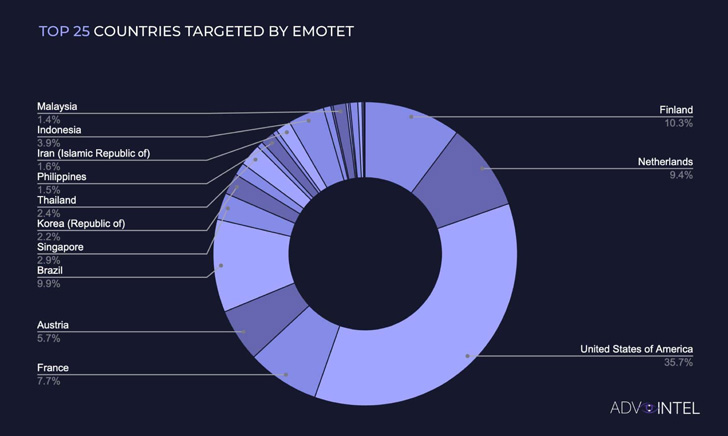
AdvIntel said it observed over 1,267,000 Emotet infections across the world since the start of the year, with activity peaks registered in February and March coinciding with Russia’s invasion of Ukraine.
A second surge in infections occurred between June and July, owing to the use by ransomware groups such as Quantum and BlackCat. Data captured by the cybersecurity firm shows that the most Emotet-targeted country is…