Ransomware Attacks on the Rise Globally and in Israel
Ransomware attacks are becoming increasingly common globally, including in Israel. The recent attack on the Mayanei Hayeshua hospital did not come as a surprise to Bobi Gilburd, Chief Innovation Officer at Team8 and former commander of the 8200 unit’s Cyber Center. Gilburd explains that the key difference lies in an organization’s response and recovery. While some businesses are severely impacted and may even be forced to close, others are able to recover swiftly.
According to Gilburd, ransomware attacks are on the rise, in part due to the introduction of generative artificial intelligence. He emphasizes that the answer to AI-driven attacks is AI itself. Gilburd encourages the use of AI-enhanced security products to counter evolving threats.
Ransomware attacks are widespread globally and are not specifically targeted at certain institutions. Attackers use malware to scan thousands of websites for vulnerabilities. While most attempts may fail, a small percentage may succeed. When conducted on a large scale, these attacks can affect numerous sites.
The attacks often start with phishing, where employees are tricked into opening malicious emails or visiting malicious websites. Education can help prevent such attacks by teaching people how to identify unusual elements in emails. Automatic tools can also block such emails at the corporate level.
If an employee falls victim to a phishing attack, automatic protection products play a role in detecting unusual domain requests and halting the attack. However, in some cases, these defense mechanisms may fail due to outdated or insufficiently powerful products or the exploitation of zero-day vulnerabilities.
When the attack successfully infiltrates the network, protection products within the network should prevent movement between computers and unauthorized access. In the case of Mayanei Hayeshua, this defense mechanism appears to have failed, leading to the widespread spread of the attack.
Once the attack is noticed, affected computers become unresponsive, and the ransomware spreads from one computer to another, encrypting databases. This process can take hours, providing an opportunity to halt the attack by shutting down the server and…



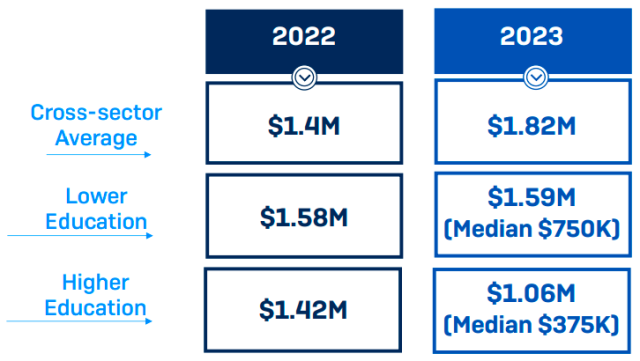
 The ability to recover encrypted data is crucial for organizations facing ransomware attacks. Fortunately, all higher education institutions and 99 percent of lower education organizations were successful in recovering their data. Notably, the recovery rate for the education sector surpasses the cross-sector average, indicating a degree of resilience in the face of such threats.
The ability to recover encrypted data is crucial for organizations facing ransomware attacks. Fortunately, all higher education institutions and 99 percent of lower education organizations were successful in recovering their data. Notably, the recovery rate for the education sector surpasses the cross-sector average, indicating a degree of resilience in the face of such threats.