Rust-Based Botnet P2Pinfect Targets MIPS Architecture
The cross-platform botnet known as P2Pinfect has been observed taking a significant leap in sophistication.
Since its emergence in July 2023, this Rust-based malware has been on the radar for its rapid expansion, according to a new advisory published today by Cado Security.
Initially exploiting Redis for entry into systems, P2Pinfect has now unveiled a new variant specifically crafted for Microprocessor without Interlocked Pipelined Stages (MIPS) architecture, indicating a strategic shift in its targets.
This latest move signifies an alarming escalation in the botnet’s tactics, showcasing a deliberate focus on routers, Internet of Things (IoT) devices and various embedded systems. The utilization of MIPS processors in these devices makes them particularly vulnerable to the P2Pinfect threat.
Read more on this threat: Novel Worm-Like Malware P2Pinfect Targets Redis Deployments
Researchers at Cado Security Labs stumbled upon this MIPS variant while investigating files uploaded via SFTP and SCP to an SSH honeypot. Unlike earlier iterations that primarily leveraged SSH servers for propagation, this variant stands out for attempting brute-force SSH access to embedded devices.
Additionally, it was discovered that the malware could exploit Redis on MIPS devices using the OpenWRT package named redis-server.
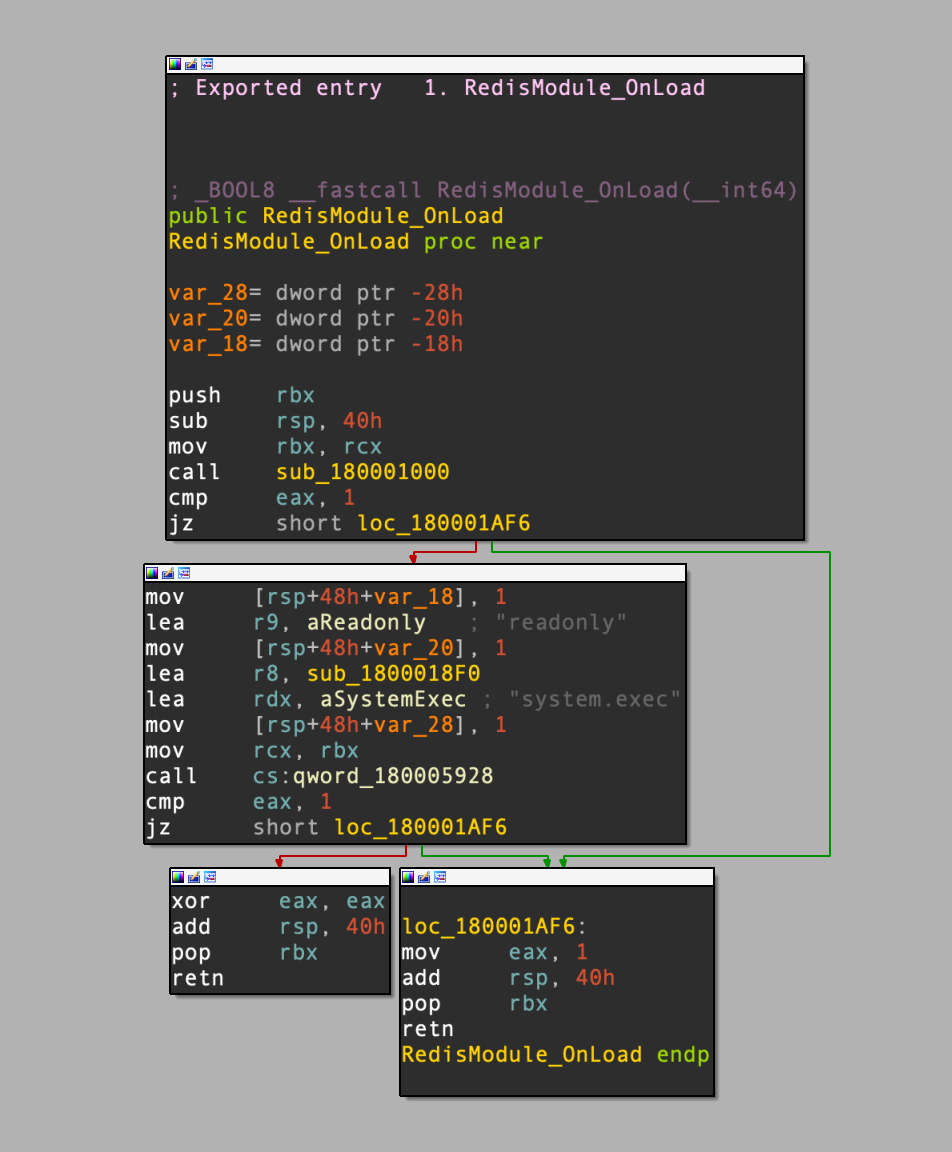
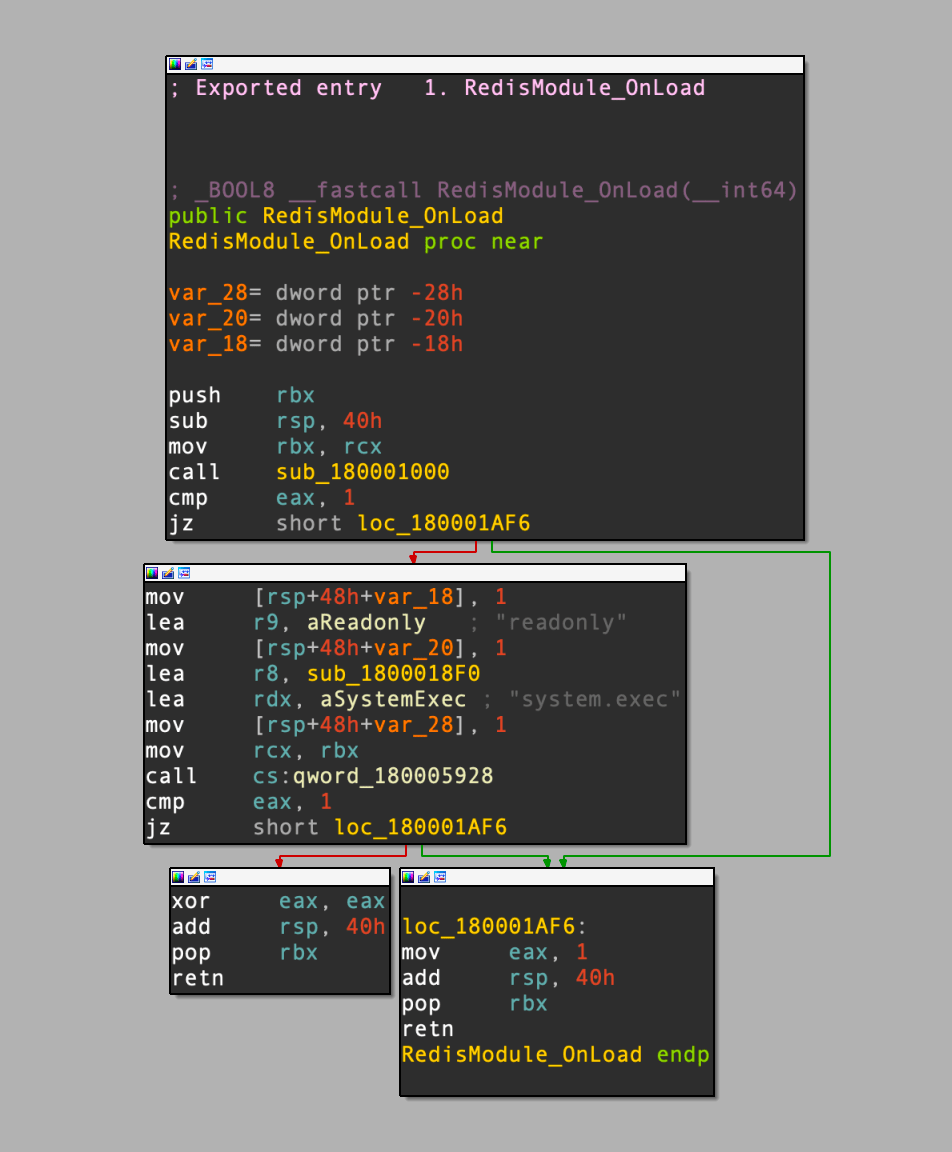
Static analysis of the MIPS variant uncovered a 32-bit ELF binary with stripped debug information, as well as an embedded 64-bit Windows DLL. This DLL functions as a malicious loadable module for Redis, introducing a Virtual Machine evasion function to complicate analysis efforts further.
What also sets this variant apart is its adoption of a new evasion technique called TracerPid, which spawns a child process to detect dynamic analysis tools. Additionally, P2Pinfect seeks to disable Linux core dumps, presumably as an anti-forensic measure to safeguard crucial information from exposure.
According to Cado Security researchers, the evolution in tactics used by P2Pinfect, combined with its expanded target range and advanced evasion techniques, strongly indicates the involvement of a determined and sophisticated threat actor.