The Dark Web Is Expanding (As Is the Value of Monitoring It)
Many security professionals today associate the Dark Web with named leaks, which are leaked credentials from employee password reuse. This is still a relevant threat; in the last six years, the Flare platform has counted over 12 billion leaked credentials. The Dark Web is rapidly growing along with the variety of cybercrime. So is the value in monitoring it.
The cybercrime ecosystem now not only includes private communications platforms like I2P and Tor but also reaches across clear websites and Telegram channels.
Dark Web Monitoring: What to Watch For
There is tangible value in monitoring the Dark Web for potential risks. Following are some of the threats you might encounter.
Infostealer Malware
Stealer logs with corporate access are likely one of the most significant vectors for data breaches and ransomware attacks today.
Infostealer variants such as RedLine, Raccoon, Vidar, Titan, and Aurora infect computers, then exfiltrate the browser fingerprint containing all the saved passwords in the browser. Threat actors then sell the results on Dark Web marketplaces or Telegram channels.
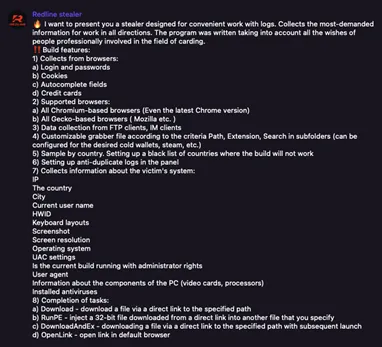
These logs are then used for account takeover attacks, stealing cryptocurrency, or as initial access for ransomware attacks. Flare monitors more than 20 million infostealer logs and is adding 1 million new logs per month, many of which contain credentials to multiple corporate applications. We believe that somewhere between 2% and 4% of logs contain access to corporate IT environments that could pose significant risk if compromised.
To detect malicious actors distributing stealer logs across the Dark Web and Telegram, companies can monitor for any logs that contain an internal corporate domain access, such as sso.companyname.com.
Initial Access Brokers
Initial access brokers (IABs) are active across Dark Web forums, such as XSS and Exploit.in. IABs establish initial access to companies, which they resell in auction and forum threads, typically for $10,000 to $500,000 per listing, depending on the company and level of access. A listing usually contains:
- Number of devices and services compromised
- Industry of the victim company
- Antivirus or endpoint…


