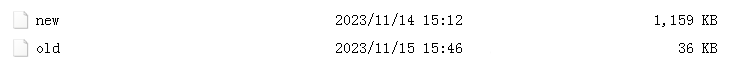xorbot: A Stealthy Botnet Family That Defies Detection
I. Background of xorbot
In November 2023, NSFOCUS Global Threat Hunting System detected that a type of elf file was being widely distributed and accompanied by a large amount of suspected encrypted outbound communication traffic. However, the detection rate of mainstream antivirus engines on this file was close to zero, which aroused our curiosity. After further manual analysis, we identified a novel botnet family with strong occultness. Given that the family uses multiple rounds of xor operations in encryption and decryption algorithms, NSFOCUS Research Labs named the Trojan xorbot.
Unlike a large number of botnet families secondary developed based on open source code, xorbot was built from scratch with a brand-new architecture. Developers attached great importance to the concealment of Trojan horses and even sacrificed propagation efficiency for better concealment effect. The latest version of Trojan horse added a large amount of garbage codes on the basis of the initial version, which increased the file volume by more than 30 times. On the traffic side, it also took painstaking efforts to randomly generate data sent during the initial online interaction stage, and introduced encryption and decryption algorithms to encrypt and store key information, thus invalidating the method of detecting character features in communication traffic.
II. Sample Analysis of xorbot
Version change
Shortly after the initial propagation version of xorbot, which first appeared in November 2023 with a file size around 30 KB, NSFOCUS Global Threat Hunting System detected another variant of the Trojan that soared nearly 30-fold to close to 1200 KB.
Through further analysis, we confirm that the xorbot Trojan communicates in the new version by introducing _libc_connect() and _libc_recv() series functions of the libc library, but the core function modules remain unchanged.
Trojan developers have added a large amount of invalid code to mask malicious branches, making the current antivirus engine detection rate close to zero. Although junk code can oversize files and affect their propagation…