Arid Viper’s AridSpy Trojan Hits Android Users in Palestine, Egypt
Cybersecurity researchers at ESET have uncovered a new Android mobile malware campaign by the Arid Viper APT group. This campaign targets Android users in Egypt and Palestine with trojanized apps distributing espionage-focused, remotely controlled AridSpy trojan.
For your information, Arid Viper, also known as APT-C-23, Desert Falcons, or Two-tailed Scorpion, is a cyberespionage group active since 2013. They target Middle Eastern countries and have a vast malware arsenal for Android, iOS, and Windows platforms. In February 2013, the group was found targeting Israelis with malware embedded in an X-rated video. In December 2020, the group returned with a new malware called PyMICROPSIA malware but its target remained the same: Israelis.
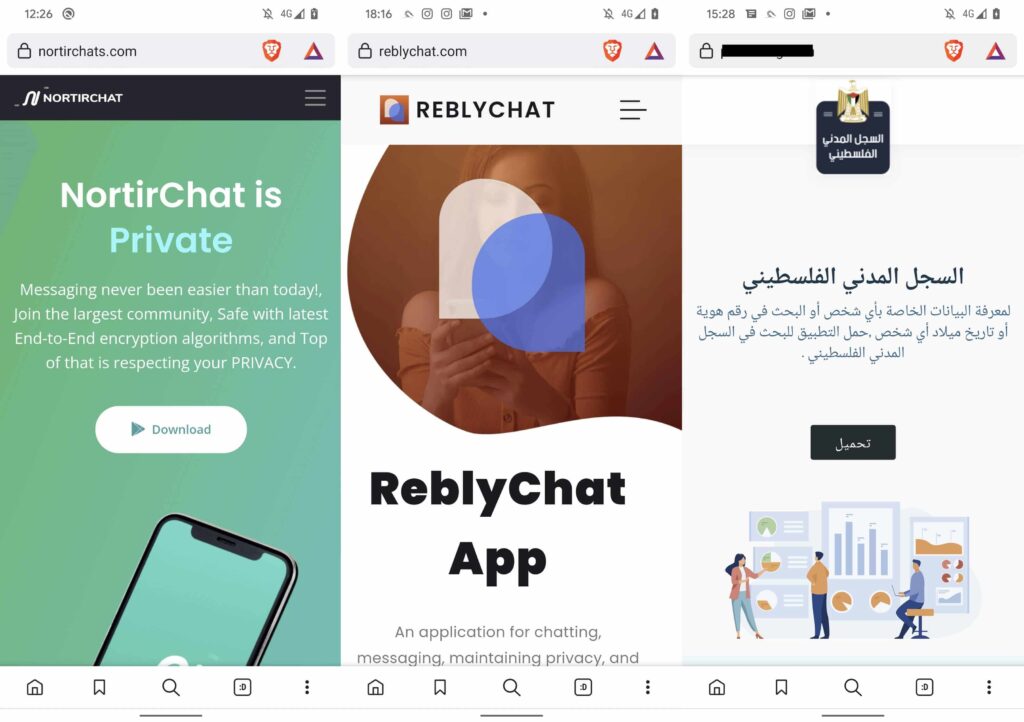
As for the latest campaign, ESET’s Lukas Stefanko explained that around five espionage campaigns have been discovered so far, three of which are still active. These campaigns distribute malicious apps impersonating messaging, job opportunities, and Palestinian Civil Registry apps, including NortirChat, LapizaChat, ReblyChat, تطبيق المشغل (Arabic job opportunity app), and السجل المدني الفلسطيني (Palestinian Civil Registry) to distribute AridSpy trojan.
These malicious apps are delivered via dedicated third-party websites, discovered using telemetry, VirusTotal, and the FOFA network search engine and not through Google. Victims must enable the non-default Android option to install them.
Six instances of AridSpy were detected in ESET’s telemetry originating from Palestine and Egypt, most registered for the malicious Palestinian Civil Registry app. In Egypt, the same first-stage payload was found with a different package name, and another first-stage payload was detected using the same C&C servers as samples in LapizaChat and job opportunity campaigns.
ESET suspects AridSpy trojan for this campaign because the group focuses on targeting organizations in Palestine and Egypt, and a malicious JavaScript file “myScript.js,” which was previously linked to Arid Viper by 360 Beacon Labs and FOFA, was detected in…