7 Emerging Ransomware Groups Practicing Double Extortion
Cybercrime as-a-service
,
Fraud Management & Cybercrime
,
Malware as-a-Service
Fresh Ransomware-as-a-Service Operations Seek Affiliates for Extorting New Victims
After a string of high-profile hits in the middle of this year, a number of the largest and most notorious ransomware operations disappeared.
See Also: Top 50 Security Threats
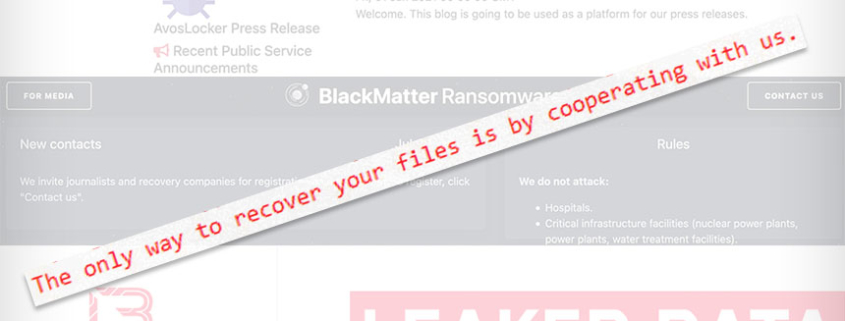
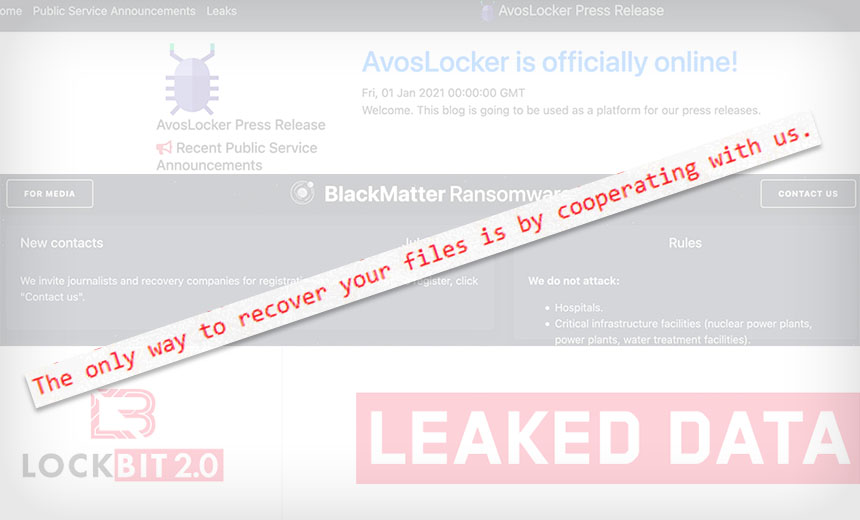
Beginning in May, ransomware attacks by Russian-language groups Conti against Ireland’s health service, DarkSide against U.S.-based Colonial Pipeline, and REvil against meat processing giant JBS and remote management software firm Kaseya led the Biden administration to try to better disrupt the ransomware business model. The White House has put Russia on notice that if it won’t disrupt ransomware-wielding criminals operating from inside its borders, then the U.S. reserves the right to do so.
In short order, DarkSide and REvil disappeared, as did Avaddon, with experts saying they appeared to be running scared. All were ransomware-as-a-service operations, in which operators develop crypto-locking ransomware and provide it to affiliates – essentially, self-employed contractors – who infect victims. Whenever a victim pays, the affiliate and operator share a prearranged split of the payoff.
Or at least that is what happens in theory. Security firm Recorded Future’s new site, The Record, recently reported that a disgruntled Conti affiliate leaked manuals and technical…