Hackers used legitimate remote help-desk tools to scam multiple US federal agencies
TL;DR: The Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) issued a joint warning that threat actors (TA) are ramping up a hacking/phishing campaign employing legitimate remote monitoring and management (RMM) software. The CISA notes that it has discovered multiple attacks within federal civilian executive branch (FCEB) networks.
In September 2022, the CISA performed audits on several FCEB networks and found them to have been victim to a “widespread, financially motivated phishing campaign.” A month later, security researchers at Silent Push reported on a “typosquatting” trojan campaign involving several trusted domains, including PayPal, Microsoft, Geek Squad, and Amazon. On Wednesday, CISA confirmed several federal staff members had fallen for the help-desk-themed phishing campaign.
“[We] assess that since at least June 2022, cyber criminal actors have sent help desk-themed phishing emails to FCEB federal staff’s personal, and government email addresses,” the alert reads.
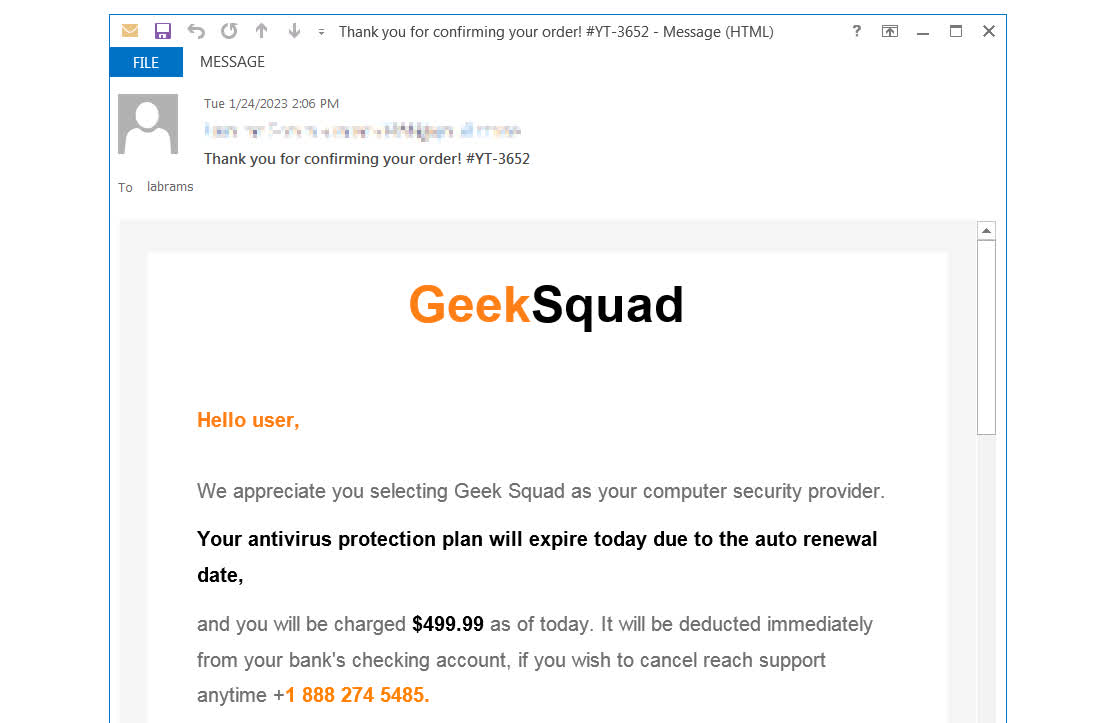
The scams are a bit more sophisticated than the typical phishing emails most people ignore. Dubbed “callback phishing,” emails are sent out that appear legitimate, like the one above from “Geek Squad.” The emails take the form of a high-priced subscription auto-renewal notice and list a number to call to cancel the automatic charge or a link to a “first-stage malicious domain.” These are pages that mimic legitimate businesses like PayPal. The URLs are also disguised, for example, paypalsec.com.
When targets call the number or visit the domain, they are convinced to download legitimate RMM help-desk software form a second stage domain, the CISA specifically named ScreenConnect and AnyDesk. The bad actors use portable executables to bypass security protections preventing employees from installing software. Portable executables are .exe files that will run without being installed on the computer, and most desktop-sharing software have these.
Once the TAs have access to the target through the RMM software, they attempt to execute a refund scam. This attack involves convincing the…


