How Hacking of The Internet of Things Works In Practice
By Milica D. Djekic
The Internet of Things (IoT) represents a collection of devices being capable to talk to each other using the internet as a communication channel. As it’s obvious – the IoT is a cyber as anything else today. That means such a technology could get vulnerable to hacker’s attacks and for such a reason it’s important to apply the good procedures and practices in order to prevent your IoT assets from cyber incidents. Through this chapter – we intend to discuss how hacking of the IoT infrastructure works in practice as well as provide some empirical examples how such a campaign could get conducted in a reality.
How we could obtain login details
Before anyone makes a decision to begin the hacker’s operation, he should try to think which information he got available as well as which tools he has. In many cases, it’s so important to adjust your hacking tool’s needs with the information being necessary for conducting a cyber campaign. The role of this learning material’s chapter is provide a closer look at some of the hacking techniques as well as a usage of cyber technologies in threatening the IoT resources. For the purpose of a good explanation of this strategy – we would use the Shodan tool that got provided some Default Passwords which could assist you in breaking into someone’s system. It’s well known that crawlers like Shodan and Censys could offer an opportunity to get anyone’s IP address and if there is no or poor authentication – anyone could make a breach or take advantage over weaknesses of that IT infrastructure. In Figure 1, we would want to show step-by-step how a Shodan could serve in obtaining so valuable login information. The illustration is given as follows.
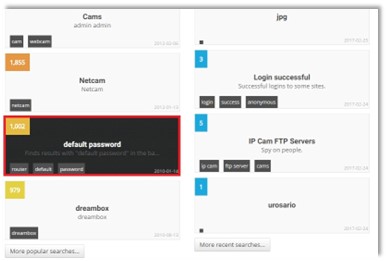
Figure 1. The Shodan’s default passwords
As it’s illustrated in the previous Figure – the Shodan would deal with many different IoT resources and one of the options would be – so called – Default Password. As it’s obvious – there would be around 1,000 devices getting its login details available to the rest of a web population. We would always highlight that a primary role of the Shodan is to serve to research’s community, but – unluckily – many…


