New Android Banking Malware Pose as Government App
Cybercriminals continue making malware for profit, with a recent report uncovering ASMCrypt in underground forums related to the DoubleFinger loader.
In the cybercrime landscape, researchers at Securelist have also reported on new Lumma stealer and Zanubis Android banking malware versions.
Researchers discovered an ad for ASMCrypt, a cryptor/loader variant designed to avoid AV/EDR detection, resembling the DoubleFinger loader.
However, researchers strongly suspect ASMCrypt is an evolved DoubleFinger version, acting as a ‘front’ for a TOR network service, though with some differences in operation.
Implementing AI-Powered Email security solutions “Trustifi” can secure your business from today’s most dangerous email threats, such as Email Tracking, Blocking, Modifying, Phishing, Account Take Over, Business Email Compromise, Malware & Ransomware
New Android Banking Malware
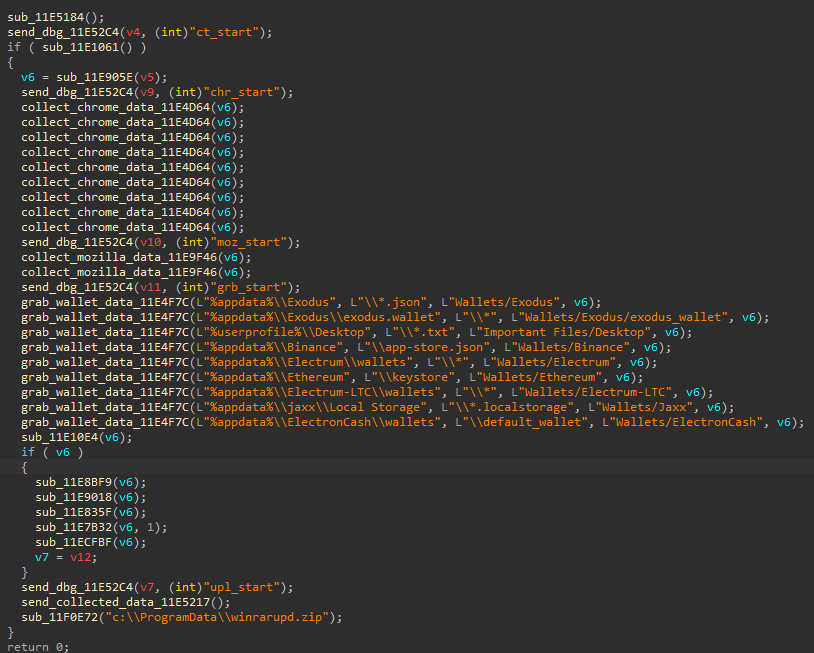
Buyers get the ASMCrypt binary, which connects to the malware’s TOR backend using hardcoded credentials and then displays the options menu.
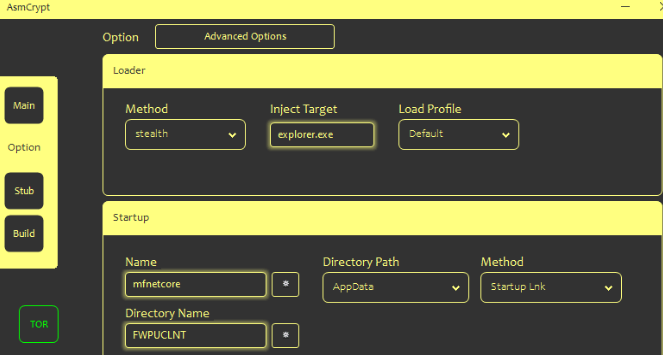
Here below, we have mentioned all the available options:-
- Stealth injection method
- Invisible injection method
- The process the payload should be injected into
- Folder name for startup persistence
- Either the malware itself masquerading as Apple QuickTime
- Either the malware itself masquerades as a legitimate application that sideloads the malicious DLL
Once options are chosen and the build button pressed, the app conceals an encrypted blob in a .png file to be uploaded on an image hosting site. Simultaneously, the cybercriminals create and distribute the malicious DLL or binary, reads the report.
- Lumma: This stealer is written in C++ and is also known by other names: Arkei stealer, Vidar, Oski, and Mars. It has maintained its core function of stealing crypto wallet data since May 2018. Lumma, with a 46% overlap with Arkei, is the latest variant, and it spreads via a deceptive website, posing as a .docx to .pdf converter, and first appeared in August 2022.