300+ gallons for $30? Men accused of using device to steal gas face felony charges
NASSAU COUNTY, Fla. – Two men accused of stealing hundreds of gallons of fuel from a 7-Eleven gas station each face a felony charge of grand theft, as well as other charges, according to the Nassau County Sheriff’s Office.
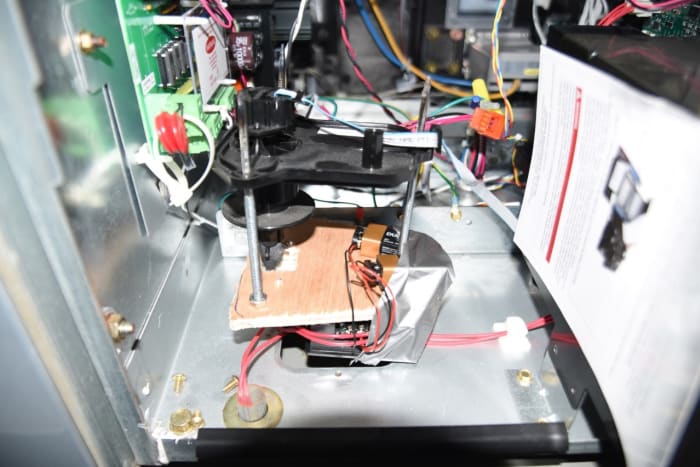
Investigators said deputies were called to the gas station Monday on Lofton Square Court, where they determined two men had installed a device on a gas pump that restricts the flow meter on its pumping system. Arrest reports state the suspects used a key to open the pumps and place the manipulator inside and then used a small remote to control the device.
According to the Sheriff’s Office, the first theft was of 367 gallons of fuel valued at $1,757.93 — but the pump only showed a charge of $30.
The Sheriff’s Office said deputies determined the same two men were involved in a second theft. Investigators said just before the deputy arrived, the men had been pumping for approximately 10 minutes and took approximately 114 gallons of gas valued at about $546.
Ad
“It was determined that the suspects opened the gas pump cabinet using a key without authorization and knowingly and willfully installed a device, which caused the electronic computer system to understate the amount of fuel being pumped,” the Sheriff’s Office reported.
The two men arrested were identified as Ramon Vila-Garcia and Silvio Richard Aguila. Both are both being held at the Nassau County jail.
We spoke with cyber security expert Chris Hamer about the device the men were accused of using.
“It was obviously designed by somebody with internal knowledge of the machines because it is custom-made for intercepting the signal from the actual fuel flow meter and modifying it or replacing it with a slower count,” Hamer explained. “So the computer thinks less gasoline is passing through the pipe than it actually is.”
Hamer said devices like the one found by investigators are used by members of organized theft rings that target gas stations all across the U.S.
Ad
“The Secret Service is currently monitoring 40 groups in Florida alone,” Hamer said. “It’s a nationwide problem. It’s a worldwide problem…