New BlackCat ransomware analysis published as leak site goes dark
Amid news that the ALPHV/BlackCat ransomware gang is shutting down operations in a likely exit scam, researchers published a new technical breakdown of the ransomware’s binary.
The Trustwave SpiderLabs report published Wednesday dives into remote access and stealth tactics used in deployment of BlackCat ransomware since the group’s resurgence, after its initial disruption by the FBI in December.
ALPHV/BlackCat’s leak site went down for a second time on Friday and is now replaced with an FBI takedown notice that security experts say is likely fake.
Inspecting the site shows the takedown banner is extracted from an archive, and Europol and the National Crime Agency (NCA) deny being involved in the takedown despite their logos appearing on the page, BleepingComputer reports.
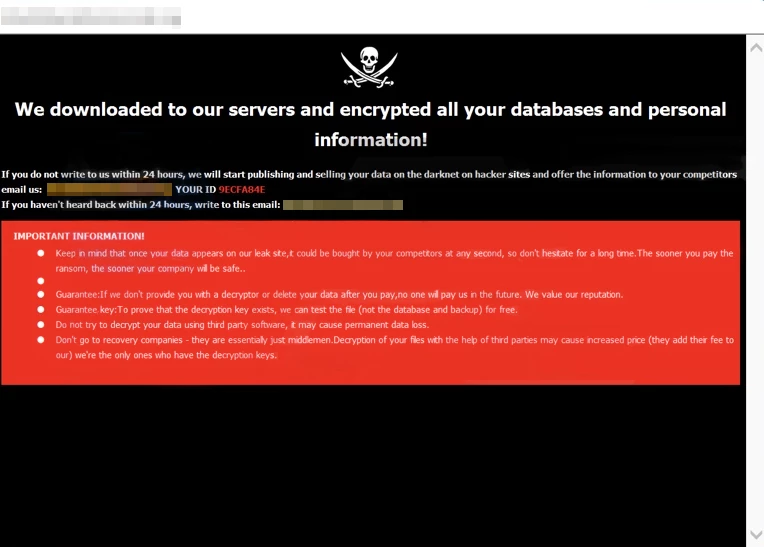
The cybergang’s operators claim they plan to cease operations and sell the BlackCat ransomware source code for $5 million due to law enforcement interference — but this move comes after allegations it stole a $22 million ransom from one of its own affiliates after claiming responsibility for the attack against Change Healthcare. This has led the gang’s actions to be labeled by many as an “exit scam.”
“Based on our experience, we believe that BlackCat’s claim of shutting down due to law enforcement pressure is a hoax. We anticipate their return under a new guise or brand after the hiatus,” Reegun Jayapaul, principal threat hunter at Trustwave, told SC Media in an email. “This tactic serves as a means for them to execute one final significant scam before resurfacing with less scrutiny.”
Whether ALPHV/BlackCat returns under a different name — or the ransomware-as-a-service (RaaS) strain is sold and brought under new management — organizations should stay alert for BlackCat’s ransomware tactics despite the bizarre shakeup.
“Regardless if BlackCat sells their source code or not, threat actors are always honing and evolving their craft,” Shawn Kanady, global director of the Trustwave SpiderLabs Threat Hunt Team, told SC Media.
New stealth features discovered in BlackCat ransomware ‘Version 3’
The BlackCat variant studied by Trustwave researchers is more elusive than previous versions…