Understanding cybersecurity management for FinTech: cybersecurity threats in FinTech (Article 3)
With a plethora of digital wallet methods, financial cyber risks such as fraudulent transactions, extortion, denial of service attacks, and credit card fraud have become frequent. These cyber-attacks are capable enough to cause systemic risk to the financial sector. Some of the most prominent cyber-attacks that the financial sector has witnessed so far have impacted critical economic infrastructures. These attacks have the potential to deliberately destroy hardware, and to compromise sensitive business data to adversely impact services.
Cybersecurity threats impact almost all the components in the FinTech ecosystem. They may pose potential exposure to various financial institutions that use technology, FinTech startups, and financial customers in the FinTech ecosystem. Technology developers also need to be aware of potential cybersecurity threats that can exercise vulnerabilities and flaws in the technology that they are developing.
This article uncovers various cybersecurity threats in FinTech and provides deep insights into categories and actors causing those threats. It also introduces the threat modelling approaches used by financial institutions to mitigate the countermeasures of these threats. The content in this article is based on the extensive research work behind our book titled “Understanding Cybersecurity Management for FinTech” published by Springer this year.
Cyber threats
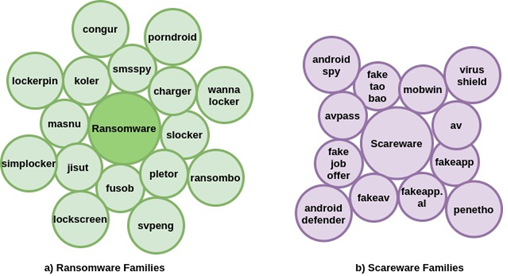
FinTech has witnessed various types of cyber threats, including malware, data breach, denial of service, cyber fraud, and phishing. Data breach and distributed denial of service (DDoS) are the two most common cyber-attacks that have been recorded on a regular basis in the timeline of cyber risks and threats on FinTech across the globe. Figure 1 below highlights the reported cyber-attacks and threats that incurred major monetary losses to financial institutions and banks between 2007 and 2019. It is evident that cyber threats pose severe risks to FinTech over the years.
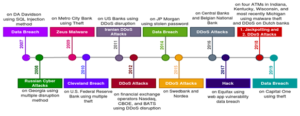
Cyber-attacks have targeted financial institutions and banks all over the world. Some recent cyber threat attempts include: hijacking famous Twitter…