Copycat researchers imitate supply chain attack that hit tech giants

This week, over 150 new packages have been published to the npm open-source repository named after private components being internally used by major companies.
These npm packages are identical to the proof-of-concept packages created by Alex Birsan, the researcher who had recently managed to infiltrate over major 35 tech firms and walk away with over six-figures in bug bounty rewards.
Within 48 hours of Birsan’s disclosure going public, copycat actors began pushing similar packages to npm, likely in a quest to earn bug bounties.
Birsan has confirmed to BleepingComputer that he is not behind these imitation packages and that these are different actors following in his footsteps.
Researcher breaches 35 tech firms in a novel supply chain attack
Recently, BleepingComputer had first reported on a supply chain attack that hit over 35 tech firms, namely Microsoft, Apple, PayPal, Tesla, Uber, Yelp, Shopify, among others.
The researcher, Alex Birsan, had taken advantage of an inherent design flaw of open-source development tools called “dependency confusion” or “namespace confusion” to squat names of private dependencies used by major companies on public open-source repos including npm, PyPI, and RubyGems.
Today, a report from Sonatype reveals, other copycat actors are now imitating Birsan’s research by flooding the npm repository with copycat packages marked “for security research purposes only.”
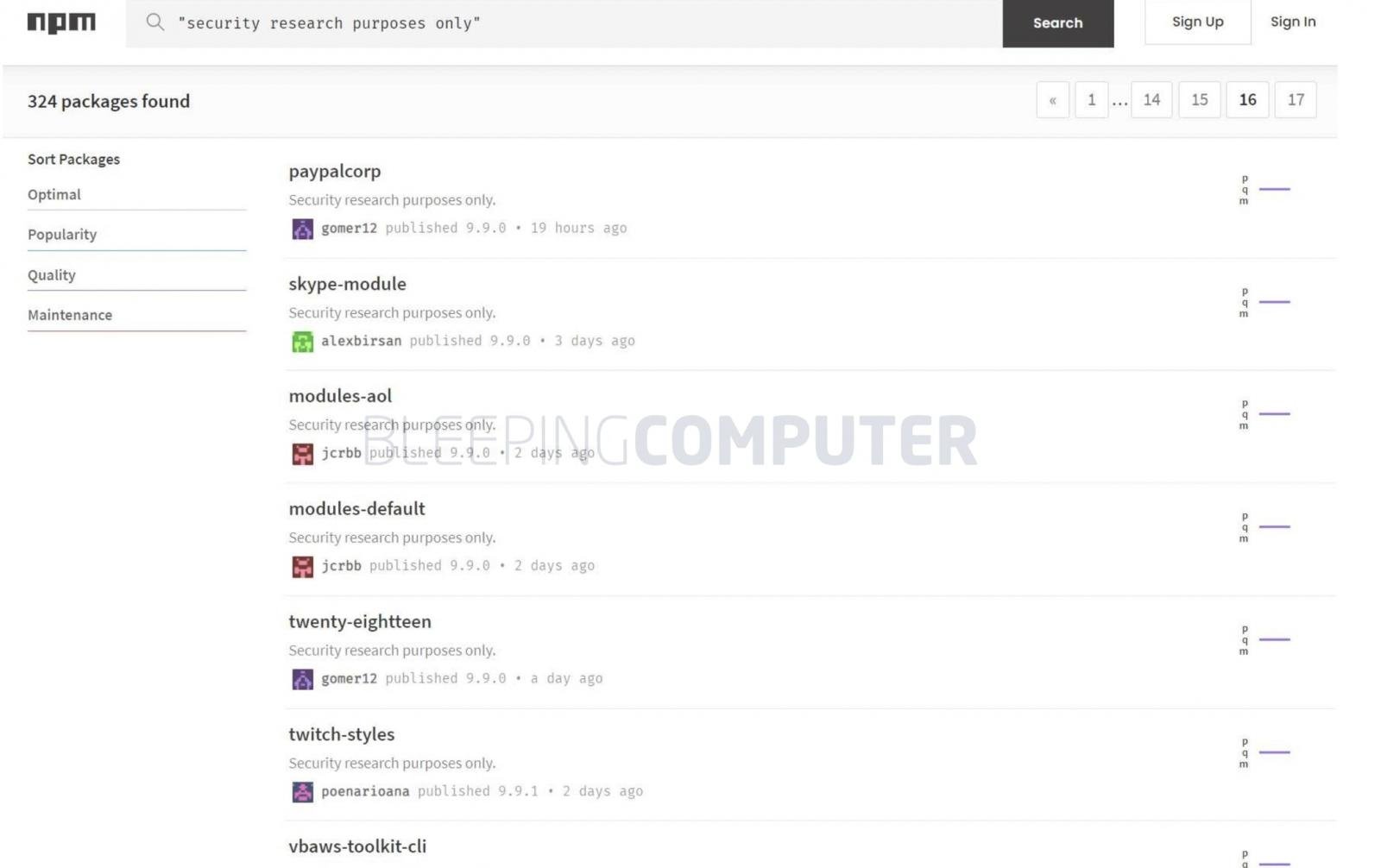
Source: BleepingComputer
Copycat actors flood npm with identical packages
Within the last 48 hours, the Sonatype Security Research team, of which I am a part, noticed a sudden spike in the volume of suspicious packages caught by our automated malware detection systems and began analyzing these packages.
And then it made sense. The vast majority of 150+ components that were flagged and are continuing to come in at the time of writing, are lookalikes of Birsan’s PoC packages that let him breach over 35-tech companies as a part of his ethical research.
But Birsan tells BleepingComputer he is not behind these copycat “research” packages, although he did admit to uploading a few more packages today under his…




