Alert: Chinese Threat Actors Exploit Barracuda Zero-Day Flaw
In recent developments, Barracuda, a prominent network and email cybersecurity firm, has been grappling with a zero-day vulnerability. The vulnerability has been identified as CVE-2023-7102 in its Email Security Gateway (ESG) appliances. The situation has been exacerbated by the active exploitation of this flaw by a Chinese hacker group known as UNC4841 Chinese. In this blog, we’ll look into the Barracuda zero-day flaw, exploring its intricacies and the consequential impact on cybersecurity.
The Barracuda Zero-Day Flaw
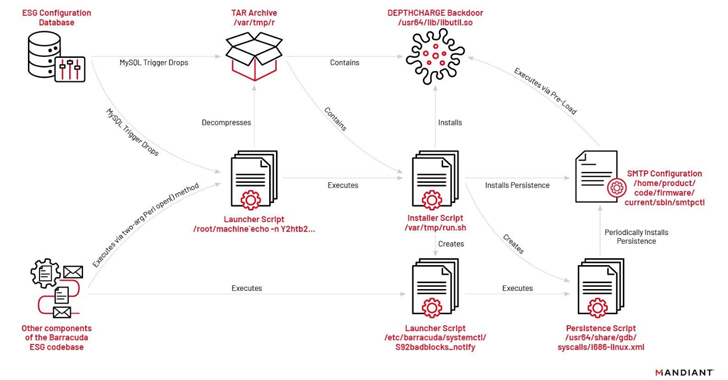
The root cause of the Barracuda ESG appliances vulnerability lies in a weakness within the Spreadsheet::ParseExcel third-party library, integral to the Amavis virus scanner running on Barracuda ESG appliances. The flaw enables threat actors to execute arbitrary code on vulnerable ESG devices through parameter injection.
Barracuda Zero-Day Flaw Exploited By Chinese Hackers
UNC4841 leveraged this Arbitrary Code Execution (ACE) vulnerability to deploy a meticulously crafted Excel email attachment, exploiting the Spreadsheet::ParseExcel library. As a result, a limited number of ESG devices fell prey to the attack, giving rise to cybersecurity threats in ESG appliances.
Barracuda responded swiftly by deploying a patch on December 22, 2023, to remediate compromised ESG appliances, which exhibited indicators of compromise linked to new variants of SEASPY and SALTWATER malware.
In the ongoing investigation of the Barracuda zero-day flaw, the organization assured customers that no immediate action is required. They also emphasized their commitment to resolving the issue and ensuring the security of ESG appliances.
CVE-2023-7101: A Wider Concern
Notably, Barracuda has filed CVE-2023-7101 for a vulnerability in the open-source library, impacting various products across multiple organizations. As of now, this concern remains unaddressed, adding an extra layer of urgency to the cybersecurity landscape.
A Recap of May’s Security Warning
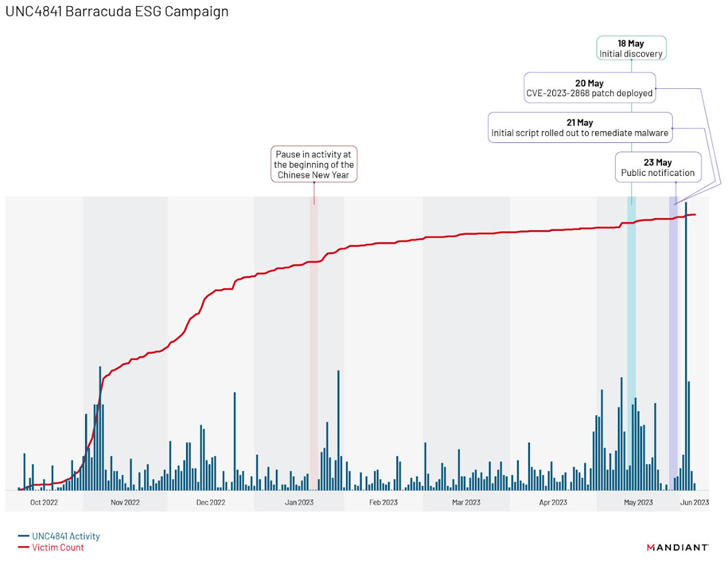
These zero-day exploits in network security devices aren’t the first time Barracuda has faced cybersecurity challenges. In May, the company issued a warning to customers about breaches in some of its Email Security Gateway…