Beware of New Trigona Ransomware Attacking FinanceIndustries
The relatively new Trigona ransomware strain, according to Unit 42 researchers, was particularly active in December 2022, targeting industries in the manufacturing, finance, construction, agriculture, marketing, and high technology industries.
“Trigona’s threat operator engaging in behavior such as obtaining initial access to a target’s environment, conducting reconnaissance, transferring malware via remote monitoring and management (RMM) software, creating new user accounts and deploying ransomware,” Unit 42 researchers.
Companies in the United States, Australia, New Zealand, Italy, France, and Germany were affected.
Specifics of the Trigona Ransomware
From the recent analysis, researchers say that unique computer IDs (CIDs) and victim IDs are included in Trigona’s ransom notes, which are presented via an HTML application with embedded JavaScript rather than the typical text file (VID).
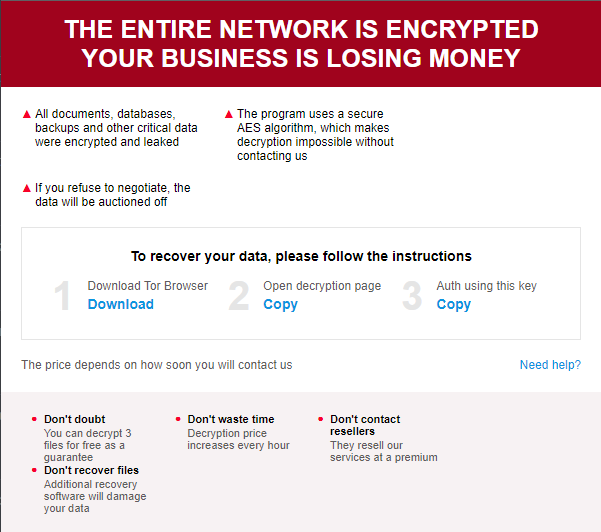
The ransom note’s JavaScript contains the following details:
- A uniquely generated CID and VID
- A link to the negotiation Tor portal
- An email address to contact.
At least 15 possible victims who were compromised in December 2022 may be found, according to experts. Also, in January 2023 and February 2023, they discovered two new Trigona ransom notes.
There was no proof that Trigona was using a leak site for double extortion when it was originally discovered. The victims were sent to their negotiating portal by their ransom message instead. A researcher identified a leak site attributable to Trigona hosted on a specific IP address.
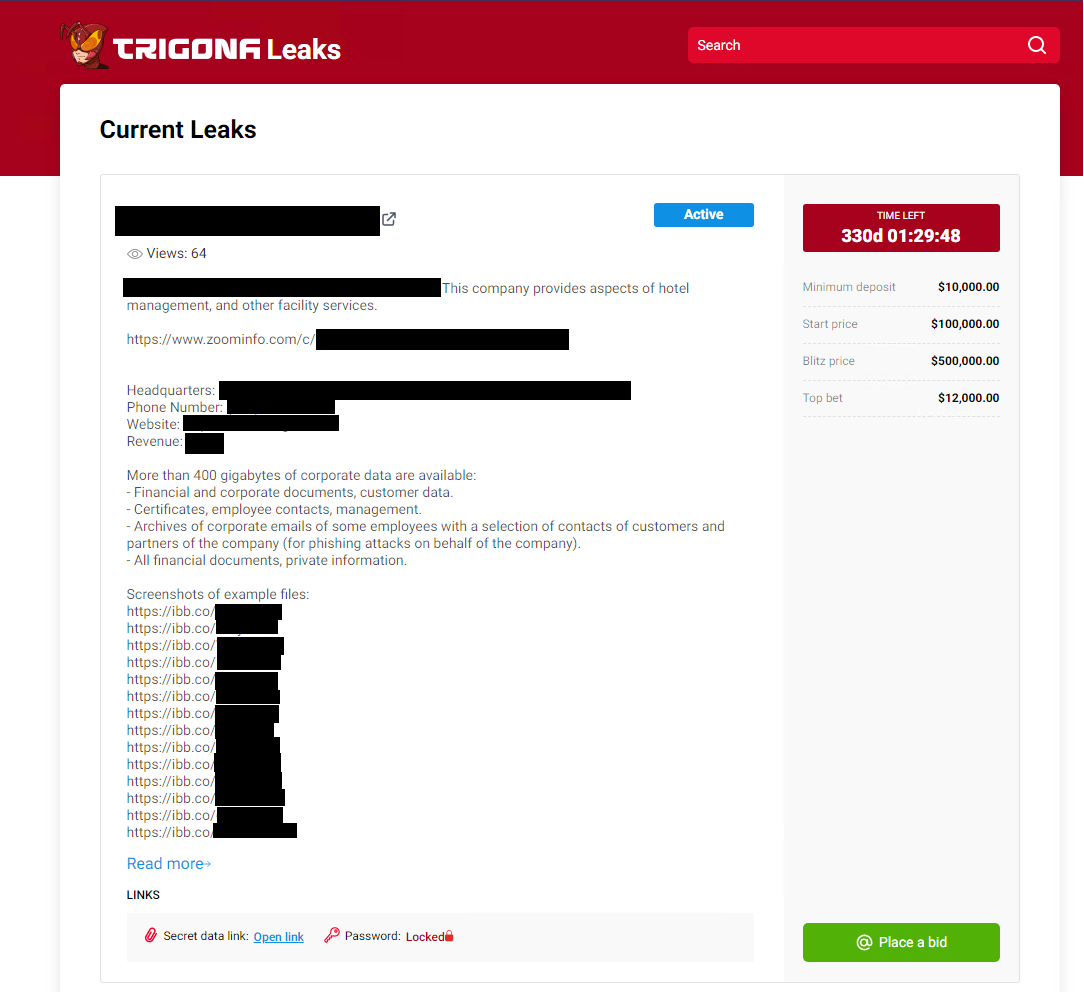
Additionally, tactics, techniques, and procedures (TTPs) used by Trigona operators and CryLock ransomware operators coincide, indicating that the threat actors who previously used CryLock ransomware may have switched to using Trigona ransomware.
Both ransomware families drop ransom notes in HTML Application format, and the ransom message is similar, including:
- Their claim that all “documents, databases, backups, and other critical” files and data were encrypted
- AES is their choice of cryptographic algorithm
- Their statement that…




