Tag Archive for: Beware
Google Chrome users ALERT! Beware of this error message, stop loss
/in Computer Security
If you are a Google Chrome user you need to be a bit careful before clicking on any of unknown links. Several security experts have warned users of a fake Google Chrome error message. Informing about the same, a blog post by Trend Micro stated, “Google Chrome users who use the browser regularly should be wary of a new attack campaign that distributes malware by posing as a Google Chrome update error message. The attack campaign has been operational since February 2023 and has a large impact area.” Another report by NTT Security has also informed of the same.
How this malware works
The malware attacks the users when they visit a legitimate or compromised website that has been infected with a malicious code, including code relating to adult sites, blogs, news sites, and online stores. As a person visits these websites, a fake Google Chrome error message will pop up asking to download an update to fix a supposed security issue.
According to the blog post, in the name of the update, what will really be downloaded is a ZIP file that has an EXE file inside. This EXE file contains a Monero miner that will use the user’s computer’s processing power to mine cryptocurrency for the attackers.
According to a report by The Sun, the prompt message reads “An error occurred in Chrome automatic update. Please install the update package manually later, or wait for the next automatic update.”
It can be known that mining crypto needs a huge amount of power, which might increase your energy bills. Notably, if you become a victim to this malware, your computer may slow down and become unresponsive. The downloaded malware also has the potential to acquire sensitive information such as log-in credentials and financial data from your computer. Most importantly, your device will be vulnerable to further malware attacks.
How to protect yourself from malware attack
Do not click on any of the prompts popping up on a website.
Be careful of what you download on your device. Always…
Google Chrome Users Beware: Zero-Day Vulnerability Exploited | Update NOW!
/in Internet Security

Google Chrome Users Beware: Zero-Day Vulnerability Exploited | Update NOW!
Type Confusion Issue in V8 JavaScript Engine
Exploit in the Wild
Google has acknowledged that an exploit for CVE-2023-2033 exists in the wild. This means that cybercriminals are actively targeting and exploiting the vulnerability. However, the company has not provided further technical details or indicators of compromise to prevent further exploitation by threat actors.
Similarities with Other Zero-Day Flaws in V8
CVE-2023-2033 appears to share similarities with four other actively abused type confusion flaws in V8 that were remediated by Google in 2022: CVE-2022-1096, CVE-2022-1364, CVE-2022-3723, and CVE-2022-4262.
Users Advised to Upgrade Immediately
Last year, Google closed out a total of nine zero-day vulnerabilities in Chrome. Users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are also advised to apply the fixes as and when they become available. This is a reminder to all internet users to stay vigilant and keep their software updated to avoid falling prey to cybercriminals.
Beware of New Trigona Ransomware Attacking FinanceIndustries
/in Internet Security
The relatively new Trigona ransomware strain, according to Unit 42 researchers, was particularly active in December 2022, targeting industries in the manufacturing, finance, construction, agriculture, marketing, and high technology industries.
“Trigona’s threat operator engaging in behavior such as obtaining initial access to a target’s environment, conducting reconnaissance, transferring malware via remote monitoring and management (RMM) software, creating new user accounts and deploying ransomware,” Unit 42 researchers.
Companies in the United States, Australia, New Zealand, Italy, France, and Germany were affected.
Specifics of the Trigona Ransomware
From the recent analysis, researchers say that unique computer IDs (CIDs) and victim IDs are included in Trigona’s ransom notes, which are presented via an HTML application with embedded JavaScript rather than the typical text file (VID).
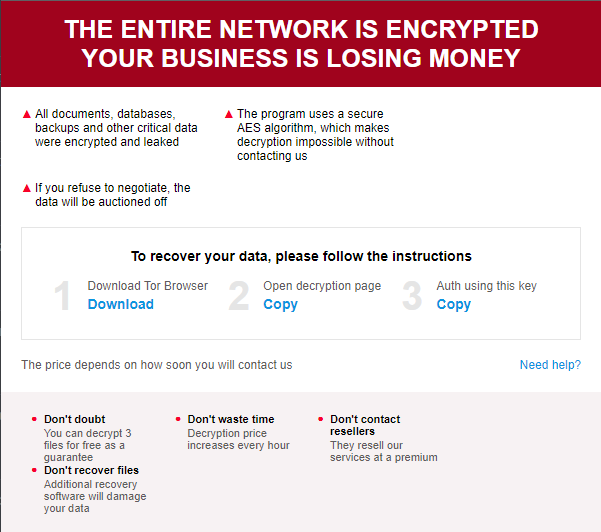
The ransom note’s JavaScript contains the following details:
- A uniquely generated CID and VID
- A link to the negotiation Tor portal
- An email address to contact.
At least 15 possible victims who were compromised in December 2022 may be found, according to experts. Also, in January 2023 and February 2023, they discovered two new Trigona ransom notes.
There was no proof that Trigona was using a leak site for double extortion when it was originally discovered. The victims were sent to their negotiating portal by their ransom message instead. A researcher identified a leak site attributable to Trigona hosted on a specific IP address.
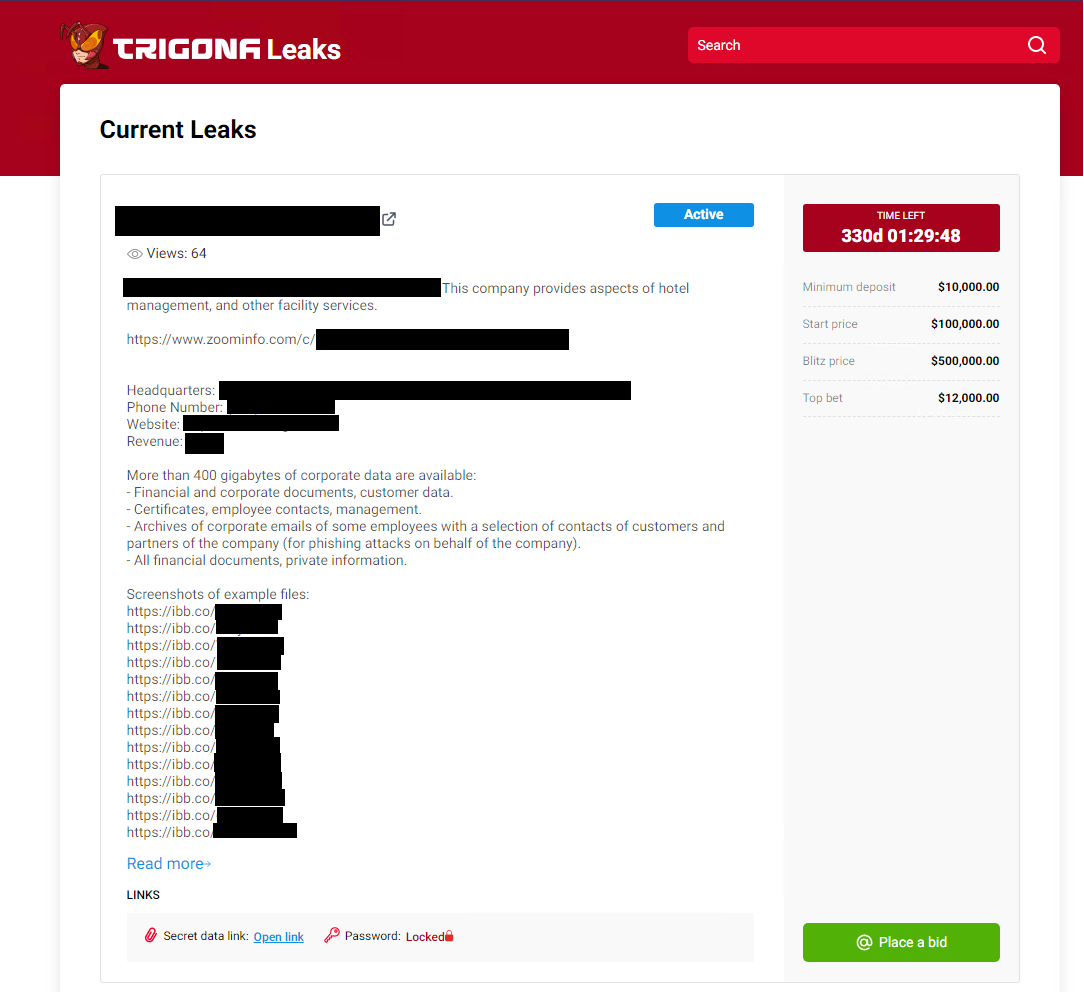
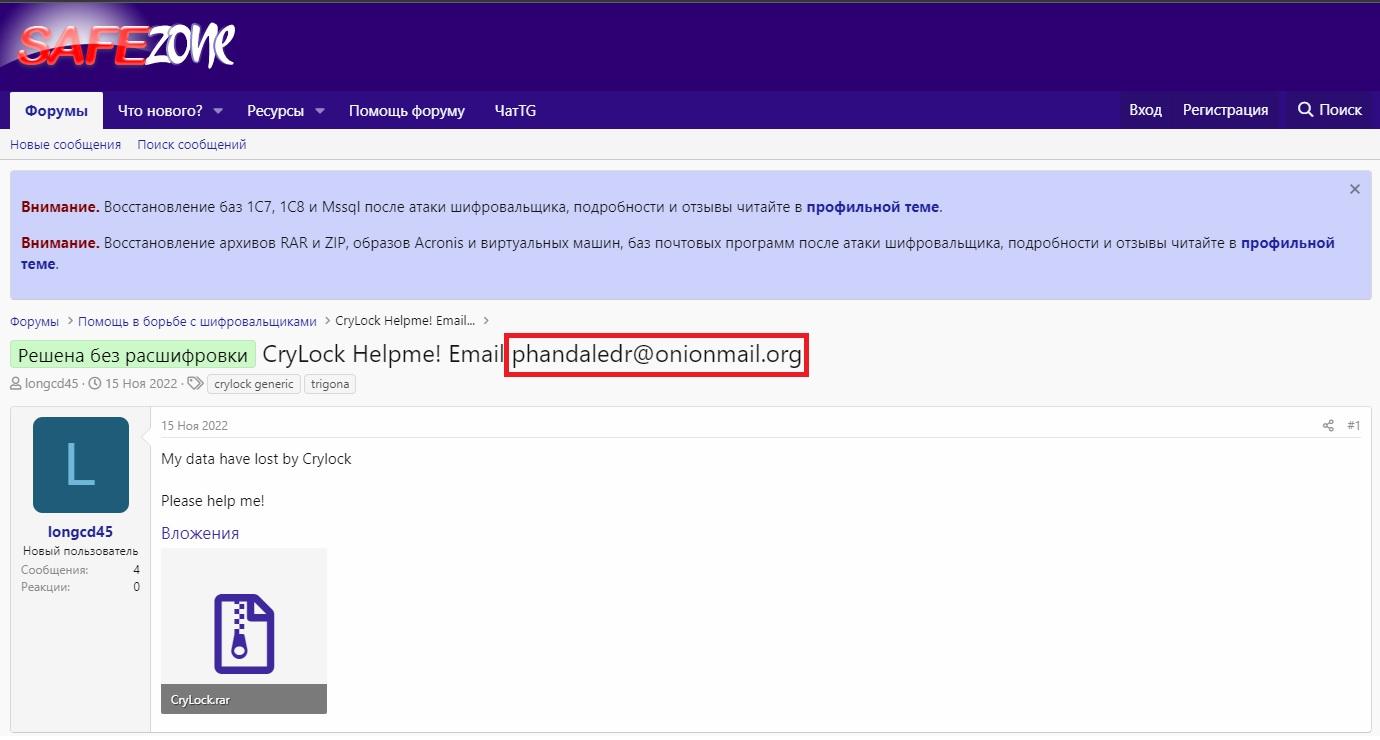
Additionally, tactics, techniques, and procedures (TTPs) used by Trigona operators and CryLock ransomware operators coincide, indicating that the threat actors who previously used CryLock ransomware may have switched to using Trigona ransomware.
Both ransomware families drop ransom notes in HTML Application format, and the ransom message is similar, including:
- Their claim that all “documents, databases, backups, and other critical” files and data were encrypted
- AES is their choice of cryptographic algorithm
- Their statement that…




