Opera MyFlaw Bug Could Let Hackers Run ANY File on Your Mac or Windows
Cybersecurity researchers have disclosed a security flaw in the Opera web browser for Microsoft Windows and Apple macOS that could be exploited to execute any file on the underlying operating system.
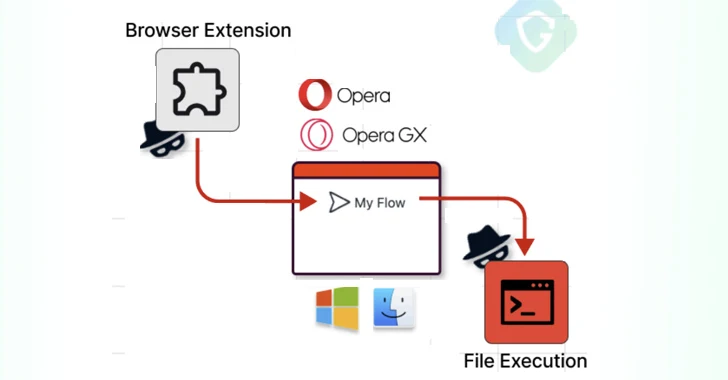
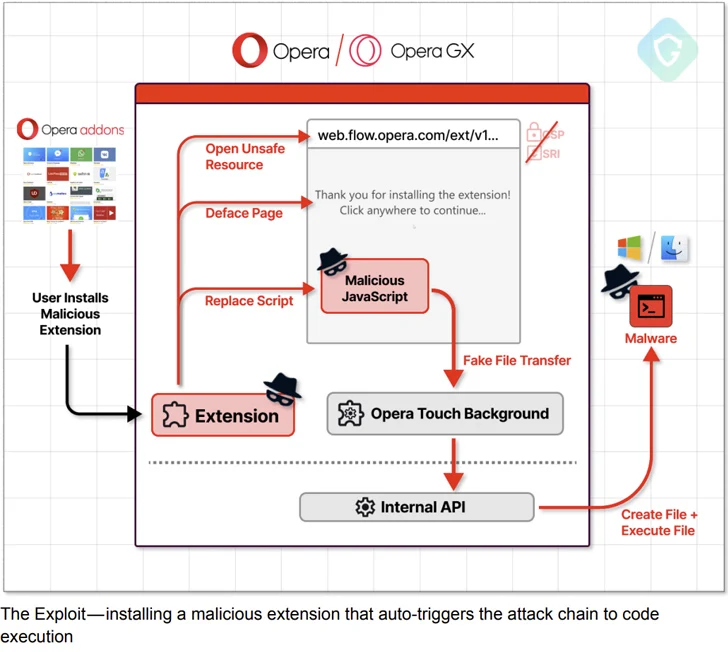
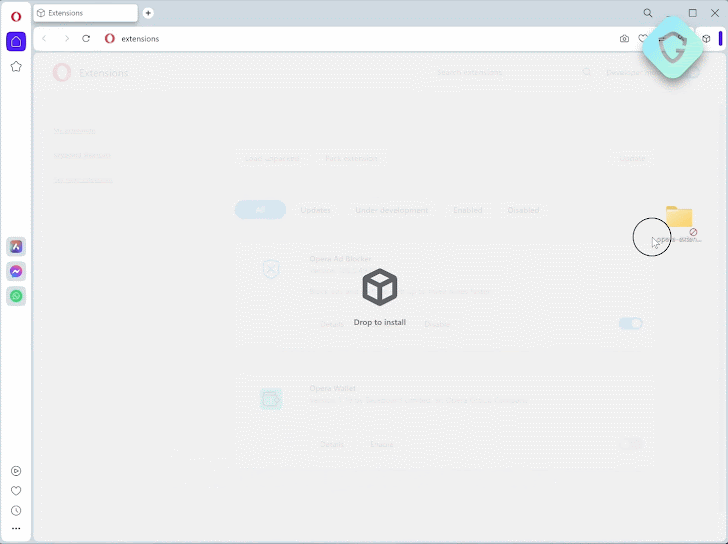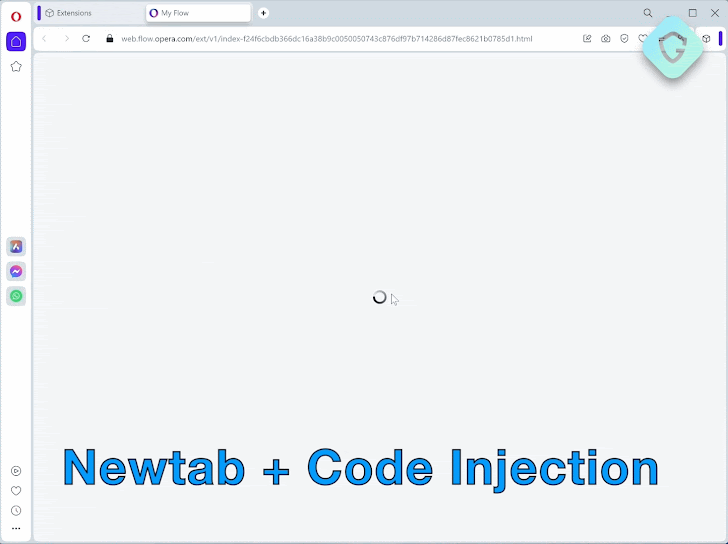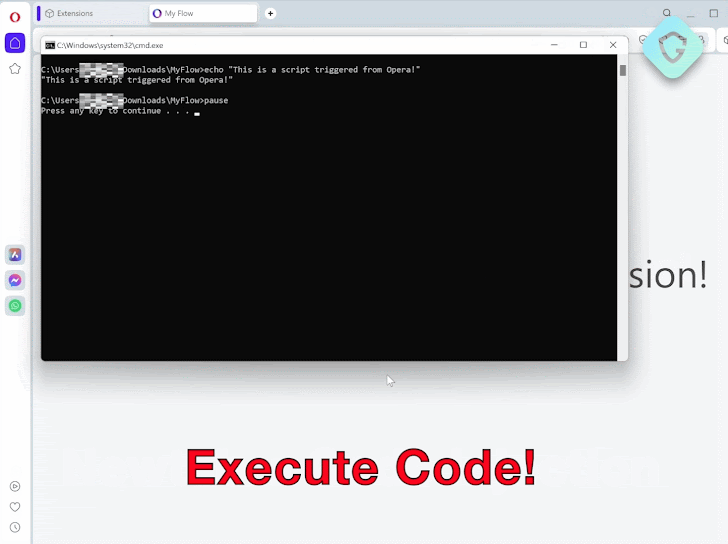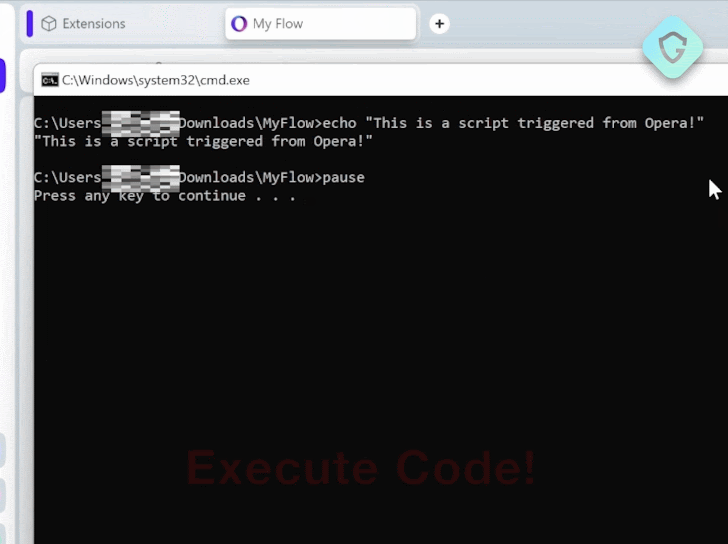
The remote code execution vulnerability has been codenamed MyFlaw by the Guardio Labs research team owing to the fact that it takes advantage of a feature called My Flow that makes it possible to sync messages and files between mobile and desktop devices.
“This is achieved through a controlled browser extension, effectively bypassing the browser’s sandbox and the entire browser process,” the company said in a statement shared with The Hacker News.
The issue impacts both the Opera browser and Opera GX. Following responsible disclosure on November 17, 2023, it was addressed as part of updates shipped on November 22, 2023.
My Flow features a chat-like interface to exchange notes and files, the latter of which can be opened via a web interface, meaning a file can be executed outside of the browser’s security boundaries.
It is pre-installed in the browser and facilitated by means of a built-in (or internal) browser extension called “Opera Touch Background,” which is responsible for communicating with its mobile counterpart.
This also means that the extension comes with its own manifest file specifying all the required permissions and its behavior, including a property known as externally_connectable that declares which other web pages and extensions can connect to it.
In the case of Opera, the domains that can talk to the extension should match the patterns “*.flow.opera.com” and “.flow.op-test.net” – both controlled by the browser vendor itself.
“This exposes the messaging API to any page that matches the URL patterns you specify,” Google notes in its documentation. “The URL pattern must contain at least a second-level domain.”
Guardio Labs said it was able to unearth a “long-forgotten” version of the My Flow landing page hosted on the domain “web.flow.opera.com” using the urlscan.io website scanner tool.
“The page itself looks quite the same as the current one in production, but changes lie under the hood: Not only that it…