Ontario government worker charged in COVID-19 vaccination data breach
Suspects from the Ottawa and Montreal areas, one of whom worked at a government vaccination call centre, were arrested Tuesday in connection with an OPP investigation into a security breach of Ontario’s COVID-19 immunization system.

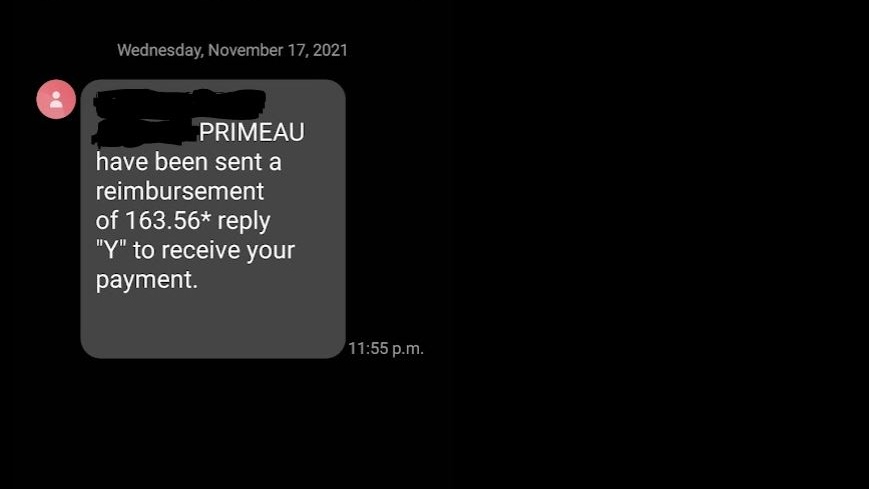
The province’s cybercrime team said it started an investigation into a possible data breach on Nov. 17 when the Ontario government flagged reports from the public about spam text messages received after residents booked COVID-19 vaccine appointments or downloaded their vaccination certificates.
On Monday, OPP executed search warrants in Ottawa as well as in Quebec with help from the Sûreté du Québec.
Police said they seized several computers and electronic devices.
Ayoub Sayid, a 21-year-old from Gloucester, Ont., is facing charges of unauthorized use of a computer. OPP said in a statement that the suspect is a government employee who worked in the province’s vaccine contact centre.
Rahim Abdu, 22, of Vaudreuil-Dorion, Que., faces the same charges.
Both accused have been released with future court dates.
A spokesperson for Ontario Solicitor-General Sylvia Jones said Tuesday that Sayid was working in the call centre through a third-party vendor, “but is no longer employed by the government.”
Spokesperson Stephen Warner also confirmed that “no personal health information was accessed” as part of the breach.
Jones told reporters on Monday that the public can feel secure in using the online vaccination portal.
Read more:
LifeLabs failed to protect personal information of millions, says B.C. and Ontario report
“When we hear of potential breaches, we investigate thoroughly,” she said at a press conference Monday.
“We have confidence in the booking system, that there are no concerns.”
An OPP spokesperson said the cybersecurity unit is still investigating to determine how…