Ransomware still a primary threat as cybercriminals evolve tactics
Trend Micro announced that it blocked 40.9 billion email threats, malicious files, and malicious URLs for customers in the first half of 2021, a 47% year-on-year increase.

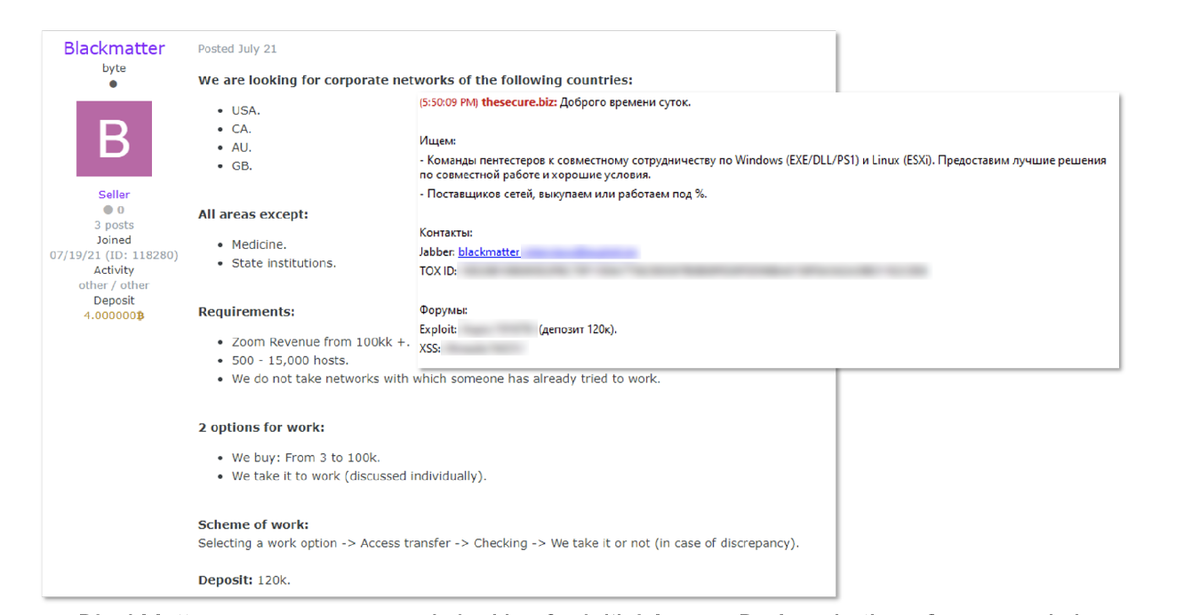
Ransomware remains primary threat in the first half of the year as cybercriminals continued to target big-name victims. Working with third parties to gain access to targeted networks, they used Advanced Persistent Threat tools and techniques to steal and encrypt victims’ data.
The banking industry was disproportionately affected, experiencing a 1,318% year-on-year increase in ransomware attacks in the first half of 2021.
Ransomware remained primary threat in H1 2021, but not the only one
Ransomware was a major threat to global organizations in the first half of 2021, but it was not the only one. The report also reveals:
- Business email compromise (BEC) attacks increased by 4%, potentially as a result of new COVID-19 opportunities for threat actors.
- Cryptocurrency miners became the most detected malware, having surged ahead of WannaCry and web shells in recent months.
- The Zero Day Initiative detected 770 vulnerabilities, a slight (2%) drop from 1H 2020.
- A total of 164 malicious apps related to COVID-19 scams were detected, 54% of which impersonated TikTok.
“The first step towards effectively mitigating cyber risk is understanding the scale, complexity, and specific characteristics of the threat landscape,” said Jon Clay, VP of threat intelligence for Trend Micro.