A Stealthy Multi-Platform Malware Leveraging NKN for DDoS Attacks

The NKN Technology Landscape:
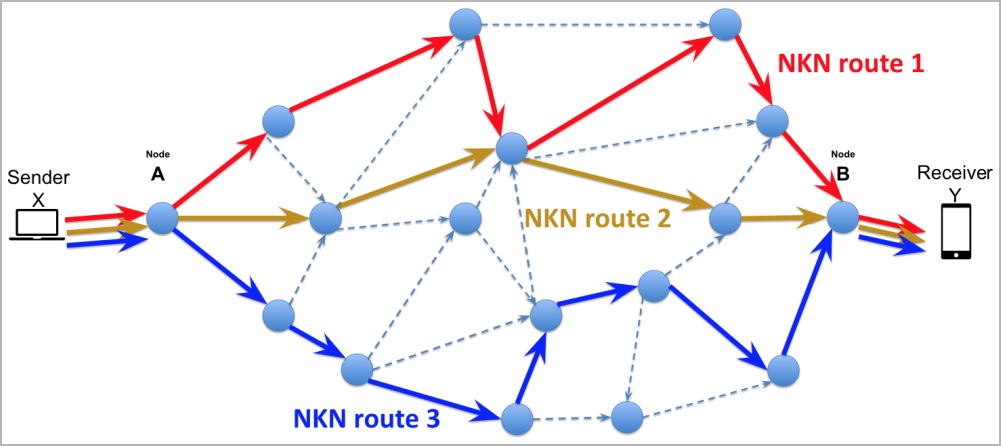
NKN, a decentralized peer-to-peer network protocol, operates by leveraging blockchain technology to efficiently manage resources and establish a secure and transparent model for network operations. With the primary goal of optimizing data transmission speed and latency across the network, NKN achieves this by calculating efficient data packet travel paths. Individuals can participate in the NKN network by running nodes, contributing to its robustness, decentralization, and capacity to handle high volumes of data.
NKAbuse: Targeting Linux Systems in Specific Regions:
Kaspersky reports the discovery of NKAbuse, a novel malware that primarily targets Linux desktops, with notable infection instances identified in Mexico, Colombia, and Vietnam. The malware exploits an old Apache Struts flaw (CVE-2017-5638) to compromise Linux systems, demonstrating its adaptability by supporting multiple architectures, including MIPS, ARM, and 386.
NKN Exploitation for DDoS Attacks:
NKAbuse stands out by abusing NKN to launch DDoS attacks, characterized by their difficulty to trace and likelihood of evading detection by conventional security tools. The malware utilizes the NKN public blockchain protocol to execute flooding attacks and establish a backdoor within Linux systems. Its communication with the bot master through NKN allows it to send and receive data, while the ability to maintain multiple concurrent channels adds resilience to its communication line.
Versatile Capabilities: A Unique Threat in the DDoS Botnet Space:
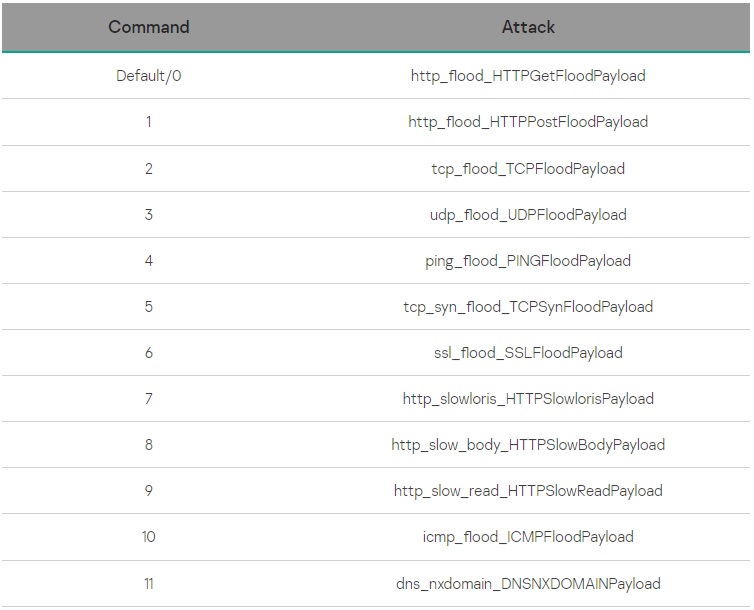
Beyond its DDoS capabilities, NKAbuse functions as a remote access trojan (RAT) on compromised…


