Latvia says Russian hackers tried to phish its Ministry of Defence
Russian hackers are being blamed for an attempted phishing attack against the Latvian Ministry of Defence.
Gamaredon, a Russian state-sponsored cyberespionage group, used a domain name (admou[.]org) previously linked to the gang in previous attacks designed to steal information and gain access to networks run by Ukraine and its allies.
Researchers at French security outfit Sekoia explained that the hackers sent spear phishing emails to the Latvian MoD while posing as officials of the Ukrainian Ministry of Defence.
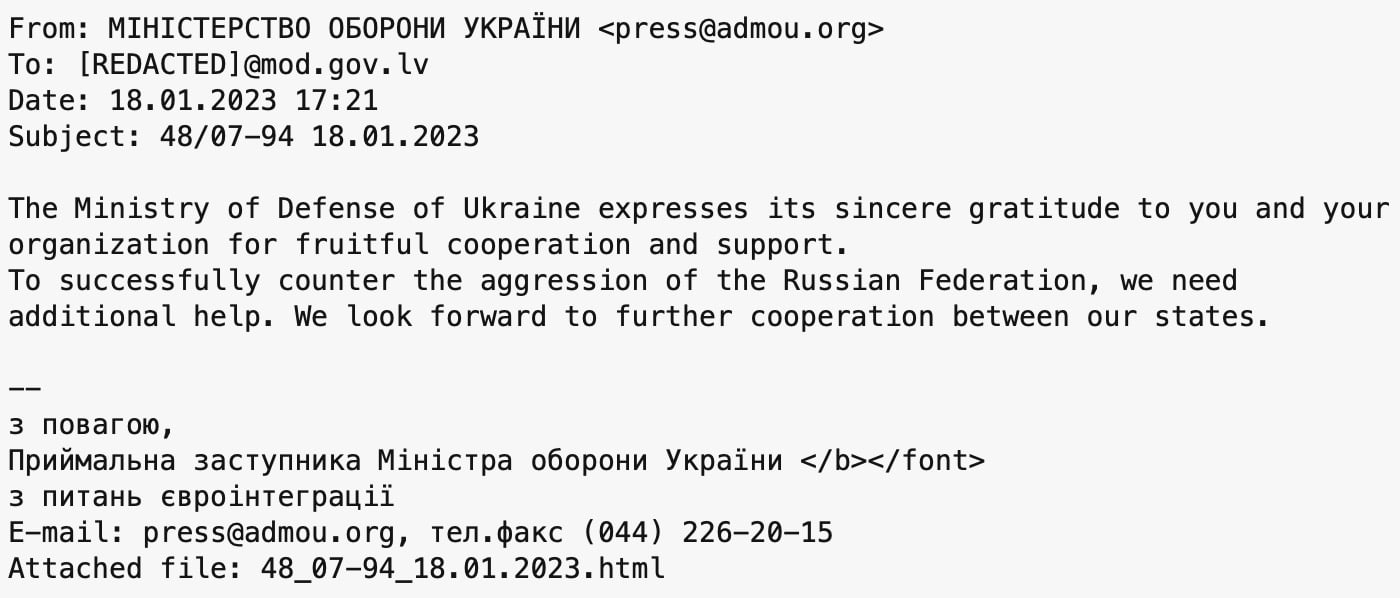
It appears that at least one of the recipients was suspicious of the message and its attachment, as it was uploaded to the VirusTotal service for scanning.
Smuggled inside the email attachment was malicious code which launched a sequence of processes, designed to help hackers steal information from their intended targets within Latvia’s Ministry of Defence.
As The Record describes, what made the investigation into the attack unusual is that once the Gamaredon hacking group realised its attack was being investigated, it began to communicate with the researchers:
A CERT-LV spokesperson told The Record that hackers sent a meme depicting a Russian bear holding a paw on Ukraine, while the U.S. and EU try to contain it.
FSB-linked Gamaredon (which is also known as Actinium, Armageddon, Iron Tilden, Primitive Bear, Shuckworm, Trident Ursa, and Winterflounder) has been attacking organsiations outside of Russia for at least ten years.
Last year, for instance, Gamaredon hackers reportedly attempted to hack into a petroleum-refining company located in a NATO country, and targeted military and government institutions in Ukraine with boobytrapped Word documents.
The Latvian Ministry of Defence says that the attempted phishing attack launched against it by the Gamaredon group was unsuccessful.
Latvia’s Computer Emergency Readiness Team (CERT-LV) says that cyberattacks in the country have risen 30% since the start of the war in Ukraine, with the most serious threats posed by pro-Russian hacktivists and Kremlin-backed hackers targeting critical infrastructure, businesses, and Latvia’s government.



