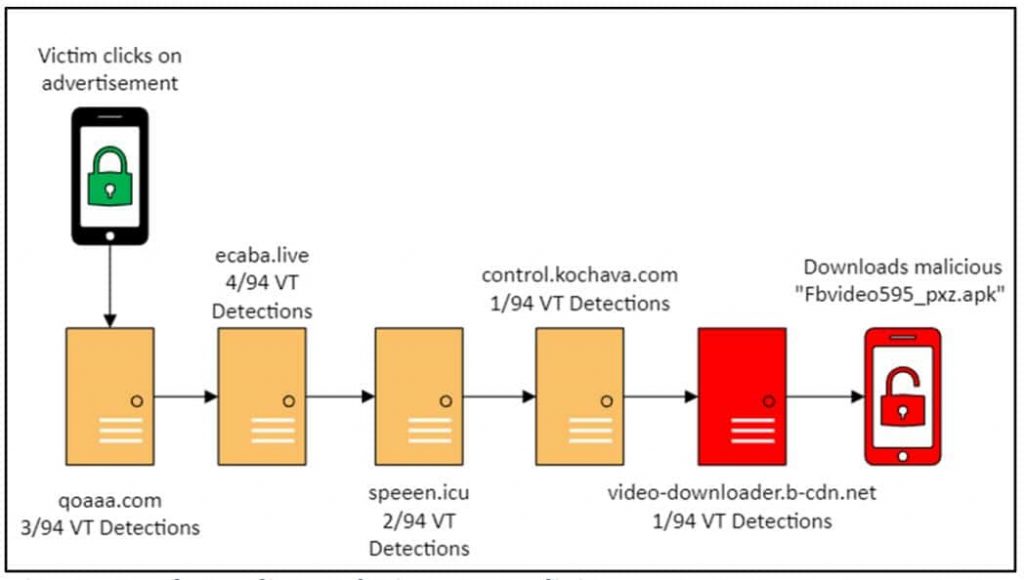
Ethical hackers discovered 65,000 software vulnerabilities this year
Check out all the on-demand sessions from the Intelligent Security Summit here.
Vulnerabilities are everywhere. Every device, application and API presents new entry points for attackers to exploit and gain access to privileged information. However, more and more organizations are turning to ethical hackers to help keep up with potential exploits.
In fact, according to HackerOne’s 2022 Hacker-Powered Security Report released today, ethical hackers discovered more than 65,000 software vulnerabilities in 2022, an increase of 21% since 2021.
The report found that digital transformation projects had helped contribute to an increase in misconfigurations by 150% and improper authorization by 45%.
At a high level, the research shows that ethical hacker communities have the capacity to identify vulnerabilities at scale, while highlighting that in-house security teams can’t afford to rely on traditional manual approaches to vulnerability management.
Event
Intelligent Security Summit On-Demand
Learn the critical role of AI & ML in cybersecurity and industry specific case studies. Watch on-demand sessions today.
Scaling vulnerability management with ethical hackers
The research comes as more and more organizations are feeling the pressure of managing an ever-growing number of exploits, with 66% of security leaders reporting a backlog of over 100,000 vulnerabilities, and 54% saying they’re able to patch less than 50% of vulnerabilities in their backlog.
This high volume of vulnerabilities has created the need for a more scalable approach to managing vulnerabilities, which ethical hacking and bug bounty vendors like HackerOne are providing.
“Insights from the hacking community about their experience and expectations teach organizations how to run a best-in-class program that will attract the top hackers,” said HackerOne’s CISO and chief hacking officer, Chris Evans.
“HackerOne’s vulnerability data, sourced from our 3,000 customer programs, shows organizations which…