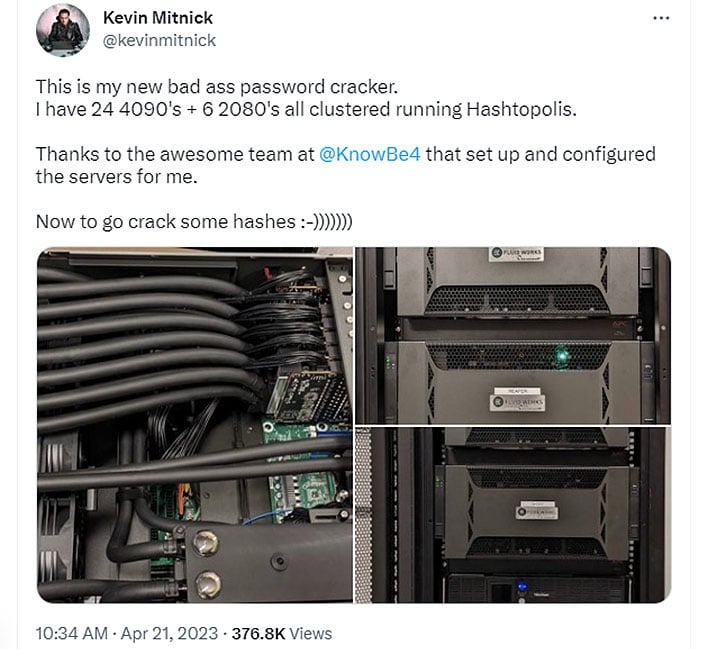
Famed Hacker Unveils Wild Crack-In-The-Box Password Cracker Fueled By Dozens Of RTX 4090s
Kevin Mitnick, a former black hat hooligan-turned-good-guy who spent several years in prison in the 1990s for various computer-related tomfoolery, is showing off a beastly setup outfitted with 30 high-end GeForce graphics cards. We know what you’re wondering—can it run Crysis? It certainly has enough firepower to push pixels around like a schoolyard bully on steroids. But what his setup is really designed to do is to crack passwords with the same speed and ease it would take Hercules to crack a walnut.
Anyone who is not familiar with Mitnick can look him up on Google or visit the Wikipedia entry on him for a quick history lesson. His hacking days started in his pre-teen years and it only gets more interesting from there. The US Department of Justice and Federal Bureau of Investigation are certainly familiar with the man who is widely considered to be the world’s most famous hacker—he eluded both agencies for years…up until he didn’t.
A successful “Free Kevin” movement helped Mitnick earn an early release after spending more than five years behind bars. These days he spends his time as a highly sought-after security consultant. He’s also the chief executive officer at Mitnick Security Consulting, and chief hacking officer at KnowBe4, among other roles on his ever-expanding resume.
In posts shared to both Facebook and Twitter, Mitnick uploaded photos of a “badass password cracker” that the team at KnowBe4 helped him set up and configure. The beastly configuration is outfitted with two dozen of NVIDIA’s flagship consumer graphics cards, the GeForce RTX 4090 based on the Ada Lovelace GPU architecture, as well as six GeForce RTX 2080 cards based on Turing.
“This is what companies come up against when we are hired for Red Team engagements. Our team now has a new large group of GPUs to crack passwords much, much faster,” Mitnick explains.
In security parlance, a Red Team engagement is essentially a simulated cyberattack. You can think of it as an intense security audit. Exposing vulnerabilities is inevitably part of the process, but that’s not the main goal. These simulated attacks test a company’s ability to detect and respond to security threats.
This process is of course…