Ransomware Group Leaks Over 1.3 Million Files In Insomniac Hack
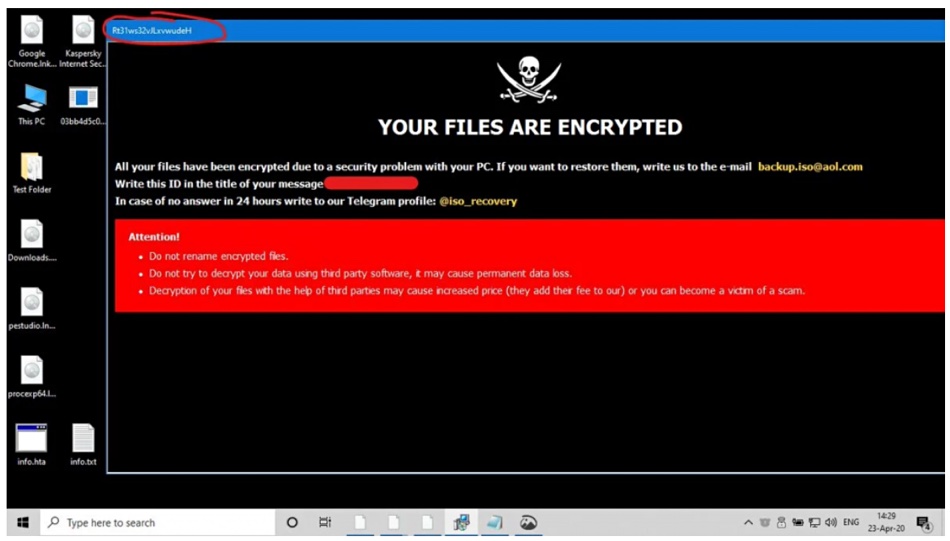
A week after ransomware group Rhysida published that it had successfully hacked into Insomniac Games and taken information, the group has published over 1.3 million files online for anyone to grab.
The full leak took place on Monday night after the group said that no buyer was willing to pay the $2 million asking price. In total, the data came in at nearly 1.7 terabytes in size.
As far as information leaked in the Insomniac hack, it ranged from game release dates and spoilers for the upcoming Wolverine game to sensitive employee information. According to Cyber Daily, that sensitive information includes internal employee HR documents, tax information, internal company messages, computer information, termination forms, and even passport details.
Also included in the data leak are contracts signed between Sony and Marvel regarding the development and publishing of X-Men games, starting with the aforementioned Wolverine title. The document was signed by both Sony’s Jim Ryan and Marvel’s Isaac Perlmutter, and went into effect as of July 2021.
In a message given to Cyber Daily, the organization said it had intentionally targetted the company, and said that it “knew developers making games like this were an easy target”. They added that it didn’t take much effort to get into the studio’s network for the data.
Insider Gaming has reached out to both Sony and Insomniac Games for comment on the leaks. As of writing, neither party has responded.