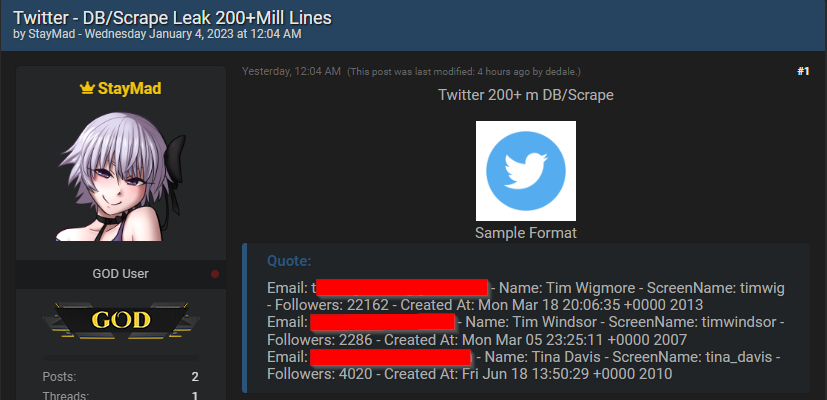
Data relating to more than 200 million Twitter Inc. users have been published on a hacking forum two weeks after data relating to 400 million Twitter users was offered for sale on the same forum.
The data is available to download from BreachForums, the successor site to the now-shuttered RaidForums. The listing describes the data as a “DB/Scrape Leak,” meaning that the data was gathered through access to Twitter and scraping public information. The database includes email addresses, names, screen names, the number of followers each Twitter user has and the date each joined Twitter.
Although the listing comes from a different user than the previously offered 400 million Twitter records, Privacy Affairs claimed today that the data appears to be from the same source. The earlier data was believed to have been gathered by exploiting an application programming interface vulnerability that Twitter fixed in January 2022.
The database includes information on notable Twitter users such as Alphabet Inc. Chief Executive Office Sundar Pichai, Donald Trump Jr. and SpaceX Inc.
Bleeping Computer reported that the database still includes duplicates. Some of the sample data provided has also been confirmed to be legitimate.
A second listing from a different user on Breach Forums claims to have taken the same data dump and cleaned it up, including removing duplicates. The second listing also claims that the records indicate that the information was collected from early November 2021 through Dec. 14, 2021.
“This is a common example of how an unsecured API that developers design to ‘just work’ can remain unsecured because when it comes to security, what is out-of-sight is often out-of-mind,” Jamie Boote, associate software security consultant at application security company Synopsys Inc.’s Software Integrity Group, told SiliconANGLE. “Humans are terrible at securing what they can’t see.”
Sammy Migues, principal scientist at Synopsys Software Integrity Group, noted that the core of the story are the issues around API security.
“As cloud-native app development explodes, so does the world of refactoring monolithic apps into hundreds and thousands of APIs and…