Ukrainian security service identifies Russian FSB officers behind Primitive Bear. US sanctions four spyware firms, including NSO Group.
By the CyberWire staff
Ukrainian security service identifies Russian FSB officers behind Primitive Bear.
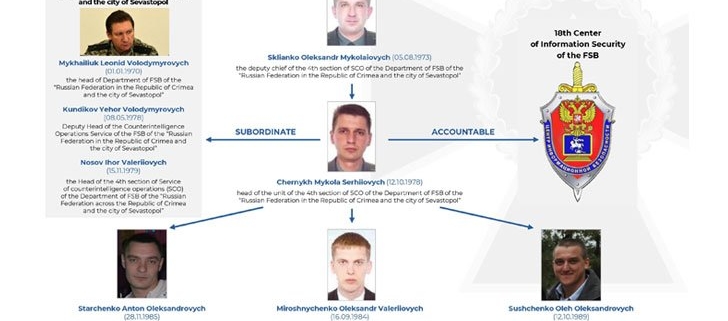
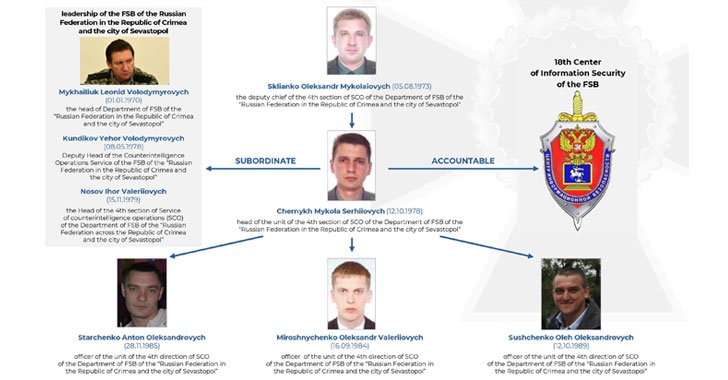
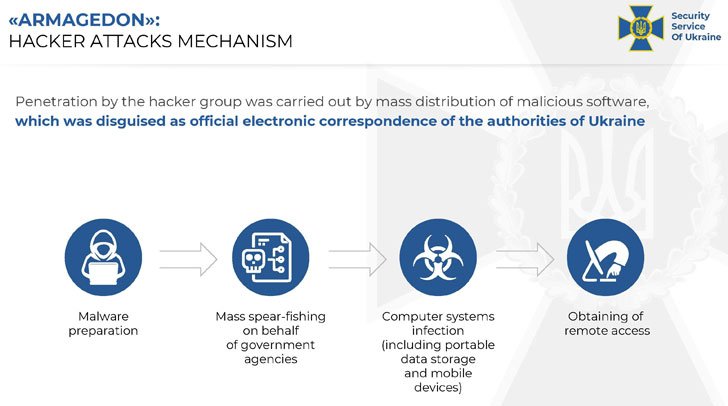
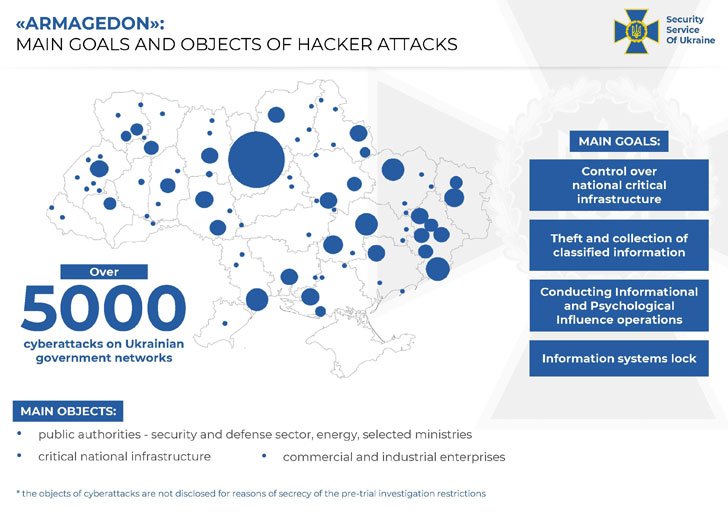
Ukraine’s security service, the SSU, has identified five Russian FSB officers as operators behind the Gamaredon threat actor (also known as “Primitive Bear”). The group has specialized in targeting Ukrainian critical infrastructure and classified networks. The group is centered, geographically, in Russian-occupied Ukraine, and the FSB chatter the SSU intercepted includes a lot of whining about getting shafted out of awards and bonuses, recognition going to the undeserving, and everybody having to get tested for COVID at work.
US sanctions four spyware firms, including NSO Group.
The US Department of Commerce has sanctioned four companies for providing spyware to foreign governments. NSO Group and Candiru (both based in Israel) have been added to the Entity List, as have Positive Technologies (a Russian firm), and the Computer Security Initiative Consultancy PTE (headquartered in Singapore).
Of the two Israeli firms, Commerce said they “were added to the Entity List based on evidence that these entities developed and supplied spyware to foreign governments that used these tools to maliciously target government officials, journalists, businesspeople, activists, academics, and embassy workers. These tools have also enabled foreign governments to conduct transnational repression, which is the practice of authoritarian governments targeting dissidents, journalists and activists outside of their sovereign borders to silence dissent. Such practices threaten the rules-based international order.”
Positive Technologies and the Computer Security Initiative Consultancy were placed on the Entity List after, Commerce said, “a determination that they traffic in cyber tools used to gain unauthorized access to information systems, threatening the privacy and security of individuals and organizations worldwide.”
The sanctions, Commerce explains, represent a move in support of human rights. “This effort is aimed at improving citizens’ digital security, combating cyber threats, and mitigating unlawful surveillance and follows a recent interim final rule released by the Commerce Department…